In the face of fluctuating commercial markets, more product companies are turning to the US federal sector for stability, expansion, and long-running contracts. With a $74B IT budget earmarked for 2024, the US Government has multiple promising avenues for sustainable growth. Uncle Sam's appetite for cloud service offerings far exceeds what the current market can fulfill, underscoring an increasingly urgent need for more FedRAMP-authorized offerings.
But what exactly does getting an authorization from the Federal Risk and Authorization Management Program entail, and how do you go about achieving it? This post covers what it means to be authorized, who needs it, and how the process works.
What Does It Mean To Be FedRAMP Authorized?
If your company offers cloud-based software services, obtaining FedRAMP Authorization enables you to sell your service to US Government agencies. Your product will be listed on the FedRAMP Marketplace for agencies to discover and learn about your offering. The service can be categorized as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS). Being FedRAMP Authorized indicates that you have met the stringent security requirements set forth by FedRAMP, ensuring your service has undergone a standardized approach to security assessment, authorization, and continuous monitoring.
FedRAMP is designed to maximize reuse, allowing other agencies to also use your service once it has been authorized by the initial agency. This approach reduces costs and time for both the government and you, facilitating the rapid expansion of your authorized service across the government sector. This feature is how a substantial one-time investment can deliver growing returns, year after year. In 2022, FedRAMP Authorized cloud products were reused more than 4,500 times across the federal government.
Moreover, FedRAMP Authorization lays the groundwork for selling services to the U.S. Department of Defense (DoD). The DoD employs a distinct process managed by the Defense Information Systems Agency (DISA), which includes defined "Impact Levels." Depending on the Impact Level, additional controls and measures may be required above and beyond FedRAMP depending on the sensitivity of the data managed by your cloud service and its intended use.
Who Needs to Be FedRAMP Authorized?
A FedRAMP Authorization is a mandatory requirement for any cloud service offering used by the US Government. It is by the FedRAMP Authorization Act as part of the 2023 National Defense Authorization Act (NDAA). This requirement applies to:
- Commercial and non-commercial cloud services
- All deployment models: public, community, private, and hybrid clouds
- All cloud service models: IaaS, PaaS, SaaS
FedRAMP requirements are included in every federal government contract involving cloud services and solutions.
The FedRAMP Authorization Process
Most companies will work with a single agency to achieve their first FedRAMP Authorization. To obtain your authorization, you must work with an agency who wants to buy your offering and is willing to support and oversee your authorization. Ultimately the agency will sign your authorization letter. Achieving a FedRAMP Authorization requires a substantial upfront investment, so identifying at least one candidate agency early in your journey is important.
Process Overview
Reviewing the published FedRAMP Authorization process can be a little confusing at first because the process is designed from the perspective of a government agency. The design assumes that your cloud service is already operational and is ready to begin the official authorization process.
ScaleSec created a simplified process for product companies who need to build and document a federal version of their cloud service. This process is broken down into four phases:
Phase 0: Launch your FedRAMP program, build and document your system
Phase 1: Begin the authorization process with your first agency
Phase 2: Get your system assessed and authorized
Phase 3: Maintain your authorization with Continuous Monitoring
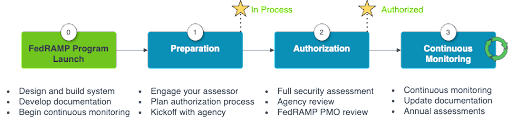
The FedRAMP Authorization Process (Agency)
Phase 0 - FedRAMP Program Launch
Before beginning the official authorization process, it's important to assess the readiness of your organization, your security capabilities, and your technology.
Some questions to help understand your readiness include:
- Does your organization formally document and enforce written security policy?
- Was your system hardened to a standard (like CIS Benchmarks)?
- Do you detect possible security breaches and manage incidents using a formal process?
- Do you have a written contingency plan, and do you test it regularly?
- Have you drawn every component of your system and its connectivity to other systems?
- Did you build your system with federally-approved cryptography?
Most companies have not considered such requirements for their commercial offering. Because of the heightened requirements, many companies opt to build a dedicated version of their offering strictly for FedRAMP use. For these reasons, ScaleSec recommends this phase for most organizations. The high level steps for this phase include:
- Design and Build Your System — Once the program plan is established, the next step is to design and build the system in accordance with FedRAMP requirements. This involves:
- Designing a target system architecture using authorized cloud services, deny-by-default policies, and least-privilege access
- Designing controls implementations to ensure coverage with all required FedRAMP security controls
- Implementing security controls to protect the confidentiality, integrity, and availability of the system and its data
- Develop Documentation — Documentation is a critical required component of FedRAMP Authorization, providing evidence of adherence to security controls and practices. This step involves:
- Preparing security documentation such as your system security plan (SSP) and Authorization Boundary Diagram (ABD)
- Documenting security controls, which detail how each required security control is implemented and managed within the system
- Maintaining an inventory of the system components, configurations, and connections
- Beginning Continuous Monitoring — FedRAMP requires that you demonstrate that Continuous Monitoring is functioning properly before you receive your authorization. This step involves:
- Installing and configuring tools like vulnerability scanning, security log monitoring, incident response ticketing, and notification systems
- Testing your plans to ensure that the critical processes for your contingency plan and incident response plan function as expected
- Providing initial required training to ensure that personnel are adequately trained and aware of their roles and responsibilities
Phase 1 - Preparation
Preparation is the phase where you officially connect with your agency, and it involves several key activities to ensure that the organization and its systems are ready for the formal assessment. This phase includes:
- Engage Your Assessor — FedRAMP requires that you work with a third-party assessment organization (3PAO), which is an independently accredited entity. Your 3PAO should join during this phase (or earlier), and will remain engaged throughout the remainder of your authorization process.
- Plan Your Authorization Process — Develop the high level plan with with your first government customer who plays a central role in coordinating efforts throughout the process. Important steps of this collaborative effort include:
- Identifying contacts for your company and the agency
- Setting a cadence for communication and collaboration with recurring meetings so all parties stay on track and remain accountable
- Communicating processes such as how you will capture and track comments and questions, how the agency will review deliverables, and how the agency will reach a decision and grant your authorization
- Prepare project documentation including your work breakdown structure (WBS), and your official request to join the FedRAMP Marketplace with the "In Process" designation and begin the FedRAMP Authorization process
- Kickoff Meeting — Hold a kickoff meeting with the FedRAMP Program Management Office (PMO), your 3PAO, and the Agency team members that will be responsible for reviewing your authorization package and making authorization decisions. During this meeting you will present your system, and you'll need technical experts on hand for any questions that arise.
- Provide an overview of your offering, including a technical walkthrough of the system, cloud services used, and its interconnections
- Present the design of your system including the authorization boundary, network architecture, and data flows
- Discuss any known gaps and your remediation plan and timeline
- Share your plan for the remainder of the authorization process including the schedule and milestones
Phase 2 - Authorization
Authorization represents the formal evaluation and approval of the system for use by the authorizing official and the FedRAMP PMO. The phase involves:
- Full Security Assessment — This first step of this phase includes a full assessment of your submitted documentation and your operational system, including:
- Your documentation package is reviewed by the federal agency who provides feedback on any concerns
- A comprehensive security assessment is conducted where the 3PAO validates your implementation of security controls, validates vulnerability scans, and performs penetration testing
- The Security Assessment Report (SAR) is developed by the 3PAO
- A Plan of Actions and Milestones (POA&M) is developed by you to document your plan and timeline to remediating any residual risk from the assessment
- Agency Review — The agency conducts a complete review of the documentation and overall readiness before submitting the package for formal authorization. This step includes:
- A documentation review is conducted by the federal agency to ensure that the authorization package clearly and accurately reflects the security posture of your offering so the authorizing official (AO) can make an informed, risk-based authorization decision
- A SAR debrief is held by you, your agency, the FedRAMP PMO, and your 3PAO to present the results of the security assessment and understand the plan and timeline for remediating any residual risk
- Remediation is likely to be required at this step for any identified documentation gaps or inconsistencies, and any open risks needed to achieve a level of risk acceptable to the AO
- Additional testing may be required as well to validate risk remediations
- Regular check-ins should be scheduled throughout the review to address any questions or concerns in real-time
- FedRAMP PMO Review and Authorization — The authorization phase involves the formal evaluation of the system by an authorizing official, who makes a risk-based decision on whether to grant authority to operate (ATO) based on the FedRAMP security controls and the organization's authorization with federal security standards. This step is designed for iterative improvements to your authorization package, with these tasks:
- The authorization review is finalized and the agency AO issues and authorization to operate (ATO)
- The AO sends your ATO letter to you and the FedRAMP PMO
- Upload your package of all authorization documentation for your system along with a checklist to the FedRAMP documentation repository
- Your 3PAO uploads your assessment material to the FedRAMP documentation repository
At this point your system is authorized for use by your first agency! You can now proceed to Phase 3 while completing the rest of this Phase 2 in parallel.
The next step is to get your system listed on the FedRAMP Marketplace so other agencies can find you.
During this part of the process your authorization enters a loop between the FedRAMP PMO, you, and your 3PAO. The PMO will review your package for gaps, clarity, quality assurance, and any concerns. You and the 3PAO will resolve these findings until the PMO decides the threshold has been reached for your system to receive the designation of FedRAMP Authorized in the FedRAMP Marketplace. This cycle may take more than one iteration, and it may require meetings with the PMO for discussions and walkthroughs to discuss any findings.
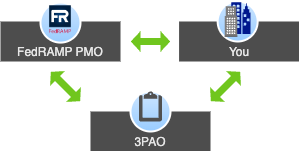
FedRAMP PMO final authorization cycle
Phase 3 - Continuous Monitoring
As described above in Phase 0, Continuous Monitoring must be demonstrated to be in place prior to receiving an authorization. After obtaining your authorization, Continuous Monitoring is a crucial aspect of maintaining FedRAMP Authorization over time to ensure that the security controls implemented during the authorization phase remain effective. To break it down further, it involves:
- Continuous Monitoring — Continuous monitoring involves ongoing observation, assessment, and analysis of security controls to identify and respond to security events and changes in the system's risk posture. This step is essential for maintaining a proactive and adaptive security posture and requires:
- Managing security events using security information and event management (SIEM) tools to aggregate and analyze log data from various sources
- Monitoring in real time, including monitoring network activities, system logs, and other relevant data to detect, triage, and investigate security incidents promptly
- Responding to incidents, following your documented incident response plan and notifying and escalating to appropriate stakeholders as described in the FedRAMP incident communications procedure
- Vulnerability scans must be conducted monthly for all operating systems, infrastructure, databases, and web applications
- Managing change control, planning and obtaining agency approval for significant changes and coordinating assessments with your 3PAO for the changes
- Meeting monthly with your agency (or agencies) to discuss POA&Ms and track vulnerability remediation to closure, discuss significant change requests, and status of your annual assessment
- Update Documentation — Policies, procedures, processes, plans, diagrams, control responses, and related documentation must be constantly updated with any changes to the system and interrelated components. In some cases this includes upgrading your entire package to align with revisions of the FedRAMP documentation and underlying standards like NIST SP 800-53.
- Complete Annual Assessments —Annual assessments involve regularly evaluating the security controls and the overall security posture of the system to identify any changes, vulnerabilities, or deficiencies that may have arisen since the initial authorization.
- Determine the scope of the annual assessment, for core controls, changed controls, and controls identified to assess once every three years
- Security assessments conducted by your 3PAO with a Security Assessment Report (SAR) to capture the process and findings
- Inherited controls must also be regularly reviewed and tracked for changes in the systems of your underlying cloud provider
- Reviewing changes, including software updates, configuration modifications, and other alterations
Conclusion
And that's all there is to it! Joking aside, this is obviously a substantial undertaking.
The key thing to remember is that getting authorized is a one-time effort with ongoing returns. And it's worth it. FedRAMP announced that in FY22 the program had over 4500 reuses for 280 cloud service providers, which means an average of 16 customer agencies for each provider. That's some serious upside. Today there are 230 total agencies listed in the FedRAMP marketplace, which presents an opportunity for 230 new customers for your cloud-based product.
If you're considering selling your cloud product to the government, we have some more reading material for you!
- Time to Upgrade your MFA for FedRAMP
- Why You Should Expand Your Sales to Include Government Entities
- Cybersecurity Executive Order: a tl;dr
- Breaking Barriers to Market Entrance with Compliance
- Why a compliance strategy should be important to executives
Get ATO-ready with Help From ScaleSec
Need help with the FedRAMP Authorization process? You’re not alone. At ScaleSec, we’ve helped many companies achieve and maintain authorization, and we can help you too.
Our programs are built for easy management, efficient operation, and support for complex, overlapping frameworks. Contact us to get started today.

