tl;dr
To meet the phishing resistance requirements for FedRAMP Moderate, we recommend you pick a hardware security key with approved encryption.
Phishing Resistance is Now Required
The updated Security Controls templates released by the Federal Risk and Authorization Management Program represent a big overhaul based on Revision 5 of the NIST SP 800-53 standard. One of the new requirements is that multifactor authentication (MFA) must be phishing-resistant. If your company is taking your commercial product to the FedRAMP Marketplace, this requirement applies to you.
 Additional FedRAMP Requirements and Guidance for Control IA-2
Additional FedRAMP Requirements and Guidance for Control IA-2
The Risk is Real
As a form of social engineering, phishing attacks us where we're the weakest - the human user. And with attackers now using Generative AI to create crafty emails, it's getting increasingly harder to detect a phish. According to Verizon, phishing represents 44% of all social engineering incidents. The FBI Internet Crime Complaint Center reported that phishing claimed a total loss of $52M in the US alone during 2022. With losses like these, it's no wonder that the NIST Zero Trust Architecture (ZTA) focuses on preventing stolen credentials by implementing phishing prevention.
How Phishing Resistance Works
In a credential replay attack, an attacker intercepts legitimate credentials between a user and an authentication service, then sends those credentials to the authentication service to log in as the user. Then, the attacker can gain unauthorized access to resources or data accessible by the user.
Phone apps are a popular form of MFA. In addition to your regular password, the app generates a unique, temporary code that you must enter to access your account known as a one-time password (OTP). This code changes every 30 seconds or so, making it harder for attackers to gain access because even if they somehow get your password, they won't have the current code the app generates. However, OTP codes can still be intercepted by unauthorized parties by intercepting communications between you and the service, phishing attacks that trick you into giving them your code, and keystroke loggers.
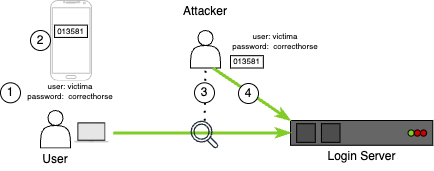
OTP codes can be intercepted
A phishing-resistant MFA prevents replay attacks by using public key cryptography, requiring your presence (like touching the device), and other techniques depending on the vendor and product. Along with your login and password, an attacker would need to have physical possession of your authentication device and, optionally, your personal PIN or biometric information. A Fast IDentity Online Universal 2nd Factor (FIDO U2F) like Yubico's YubiKey is a popular choice for a phishing-resistant MFA.
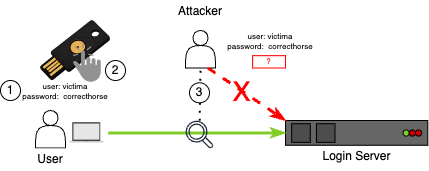
FIDO U2F authentication cannot be intercepted
It Comes From the Top
The federal requirement to use an MFA traces back to May 12, 2021 with Executive Order 14028, which included a requirement that agencies adopt Zero Trust Architecture as a part of modernizing cybersecurity for the federal government. MFA is a foundational feature of ZTA, and is included as a specific requirement. The EO directs the Office of Management and Budget (OMB) to consult with the Cybersecurity and Infrastructure Security Agency (CISA) and FedRAMP to support the modernization efforts.
Following the EO, the OMB issued Memo M-22-09, which explicitly requires phishing-resistant MFA for agency staff, contractors, and partners. The OMB memo requires agencies to implement the five pillars of CISA's Zero Trust Maturity Model. The first pillar is Identity, which includes the requirement for a phishing-resistant MFA.
Further, CISA's Zero Trust Maturity Model references NIST SP 800-207 Zero Trust Architecture, which explains the importance of phishing resistance for MFAs, and references NIST SP 800-63-B, which defines phishing resistance. SP 800-63-B also defines Authentication Assurance Levels (AAL), and requires phishing resistance for the highest rating of AAL3.
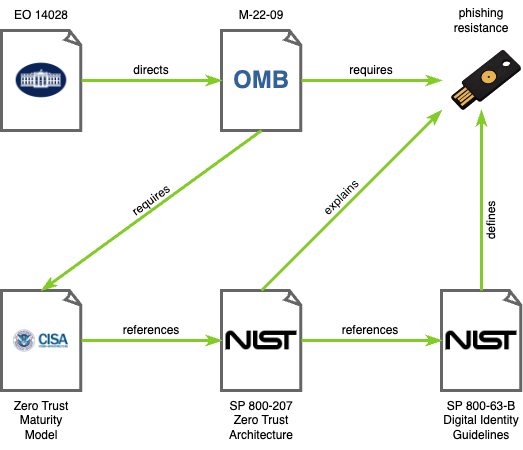
Tracing the requirement for phishing-resistant MFA
Hardware Keys are Our Favorite Choice
Phishing resistant MFA can come in a few forms, like WebAuthn, public key infrastructure (PKI), or FIDO security keys. Most federal agencies already issue a Common Access Card (CAC) or Personal Identity Verification (PIV) card to staff and partners. We think most companies will turn to hardware security keys because:
- It's a one time investment (unless you lose it).
- They're so easy to use. Once you touch the key to log in, switching back to the phone app feels clunky.
- Most major online services now support some form of hardware security key, including cloud providers, password managers, email services, developer platforms, and even some online banking systems.
Hardware keys can be lost or damaged, so we recommend buying two.
"I can’t say it enough: Give every employee a set of security keys and mandate that they use it for access to all internal services."
- Bob Lord, CISA
At ScaleSec we wholeheartedly agree with Bob, and we've been shipping YubiKeys to all new Scaliens since 2018.
Don't forget that the rest of SP 800-63B requirements apply, as noted in the IA-2 Additional FedRAMP Requirements and Guidance. This includes FIPS 140-2 or FIPS 140-3 validation for encryption, and you'll need the FIPS certificate ID for your FedRAMP package. Make sure the key model you buy meets all the requirements.
We like the YubiKey FIPS series.
References
- 2023 Verizon DBIR
- FBI IC3 2022 State Report
- Executive Order 14028 Improving the Nation’s Cybersecurity
- OMB Memo M-22-09 Federal Zero Trust Strategy
- CISA Zero Trust Maturity Model
- NIST SP 800-207 Zero Trust Architecture
- NIST SP 800-63-3
- CISA Blog: Phishing Resistant MFA is Key to Peace of Mind by Bob Lord

