HIPAA Compliance in the Cloud
Implementing HIPAA Compliance Using Cloud Infrastructure
Cloud computing brings many benefits including scalability, elasticity, and, if architected correctly, reduced responsibility for security and compliance controls that would traditionally fall on the organization. The same can be said for organizations attempting to comply with HIPAA. However, especially for this specific regulation, the loss of control that comes from adopting cloud and the shared responsibility model also brings up nuances that should be tackled early on in the architecture and design process. These considerations could even help decide which cloud service provider or specific services will be used to solution the environment.
Context and Background
The Health Insurance Portability and Accountability Act (HIPAA) is a federal law enacted in 1996. Its original purpose was to protect individuals from losing health care coverage when they changed or lost employment. However, it also includes Privacy, Security, Breach Notification, and Omnibus rules that attempt to reduce risk in the processing, transmission, and storage of “Protected Health Information” (PHI).
Despite what might be a complex regulation to interpret, HIPAA only applies to covered entities. A covered entity is defined by the US Department of Health and Human Services as a health plan, a health care clearinghouse, or a health care provider who transmits any health information in electronic form in connection with a covered transaction.
Transactions in the subchapter are defined as “transmission of information between two parties to carry out financial or administrative activities related to health care.” These include hospitals, academic medical centers, physicians, and other health care providers that electronically transmit PHI, such as claims transaction information, payment, coordination of benefits, enrollment, referrals, etc. The “Combined Regulation Text of All Rules” can be found here.
The Shared Responsibility Model
The use of a cloud service provider (CSP) effectively enters the organization into a partnership with the provider to maintain the security of the environment. The CSP is responsible for the security “of the cloud,” while the organization or customer is responsible for the security “in the cloud.” It is up to both parties to manage compliance with HIPAA, and up to the organization to build the appropriate architecture for compliance in the first place.
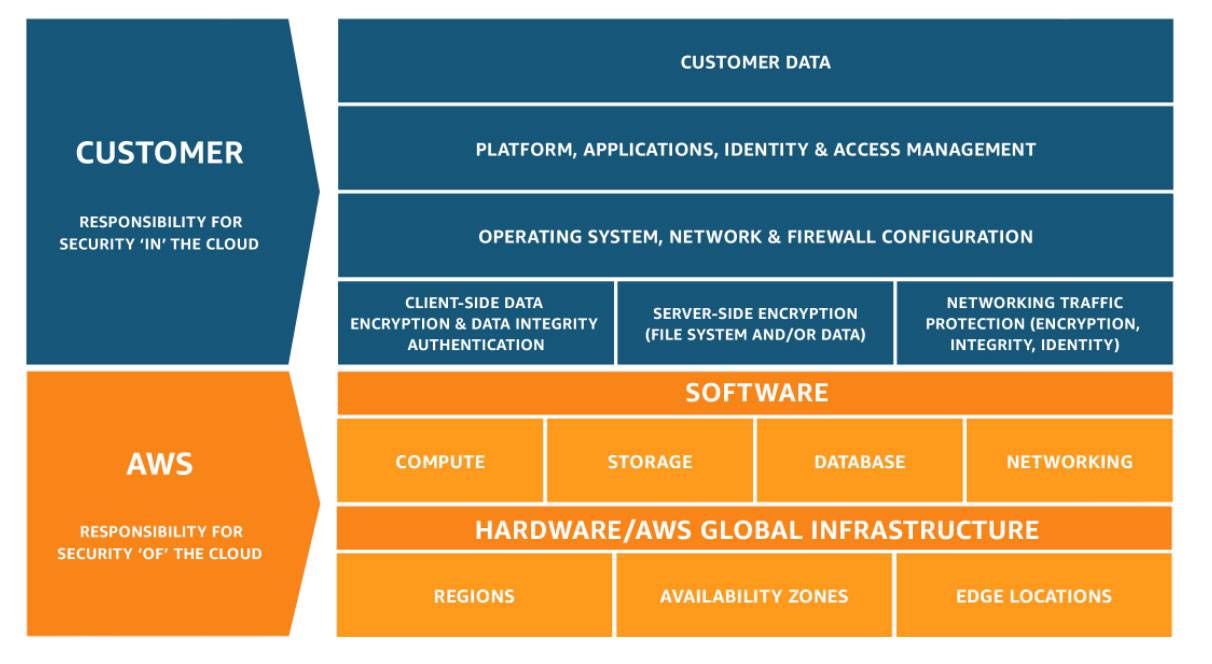
Shared Responsibility Model - Amazon Web Services
Shared Responsibility Model - Microsoft Azure
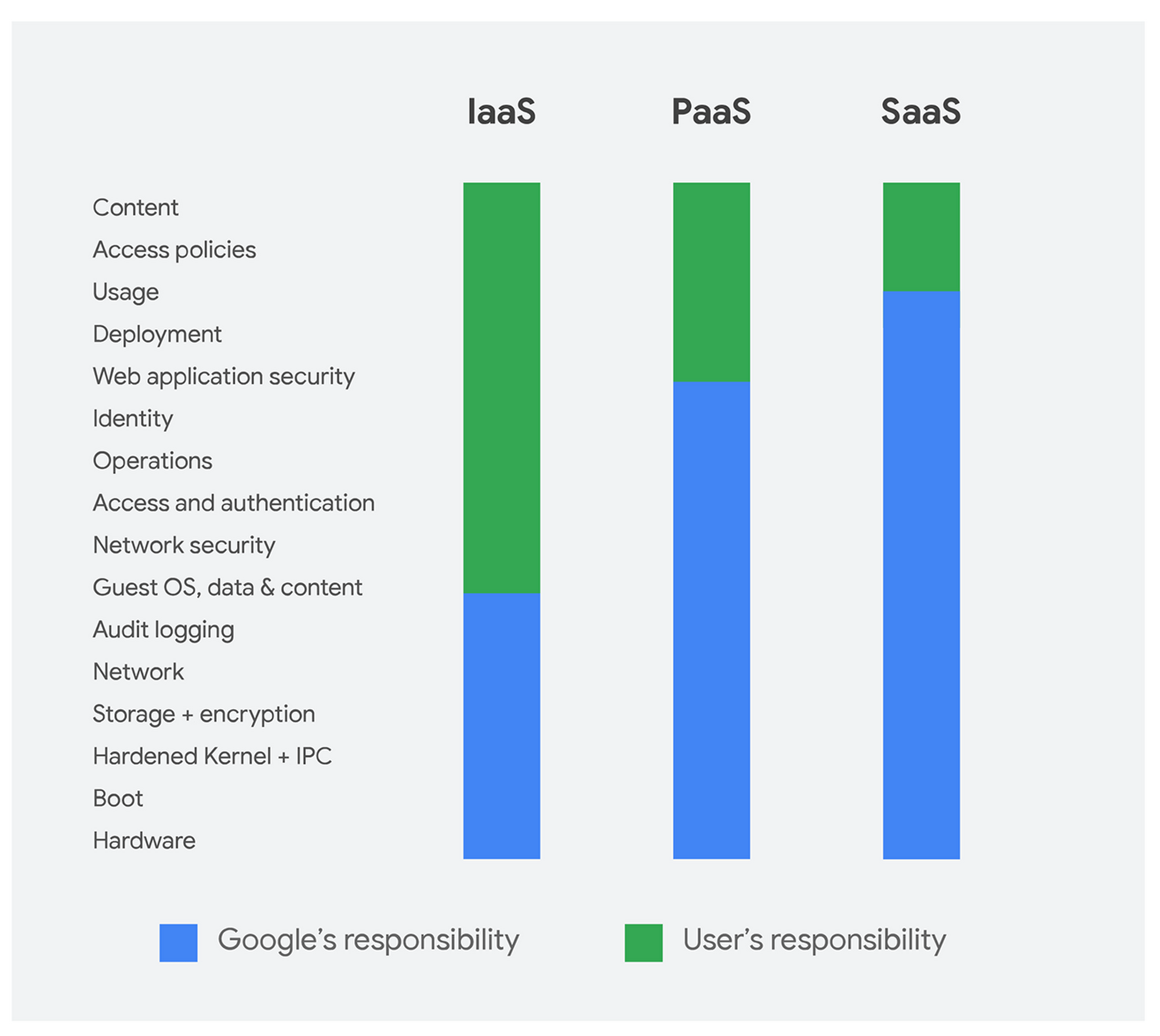
Shared Responsibility Model - Google Cloud Platform
How HIPAA Differs From Other Regulations
A few issues will have to be taken into consideration when architecting an environment to be HIPAA compliant. Below are some highlights of these issues that an organization will probably encounter.
-
First of all, there is no official HIPAA certification process offered by the government. A Covered Entity implements and documents the controls or safeguards that comply with the security rules. For a certification that can attest to these controls being in place, the organization will have to go through a regulatory audit by an organization like HITRUST.
-
Second, the guidelines can be vague and open to interpretation. There will be several ways to implement a control, and the organization will have to decide what is the most efficient and effective way to comply. In addition, the policies and practices of cloud providers and cloud services might influence decisions about how best to implement the control, so that is another consideration that the architect will have to keep in mind.
-
Third, to aid implementation, guidance on more granular controls for designing the environment are not provided by HIPAA itself. ScaleSec recommends granular implementation using NIST 800-66 as guidance, which includes a crosswalk to NIST 800-53 controls where more detail is provided on what is expected from the organization.
-
Fourth, cloud service providers have not yet made all their services compliant with HIPAA. Therefore, when architecting a compliant environment, an organization will have to use only “eligible” services, in effect, those that are identified by the CSP as HIPAA compliant.
-
Finally, HIPAA has a well-defined Breach Notification Rule, which requires Covered Entities and their Business Associates to provide notification following a breach of unsecured Protected Health Information.
Architecting HIPAA Solutions in the Cloud
Experienced IT professionals understand that architecting security and compliance when designing the environment is much easier than trying to “bolt on” security and compliance after the fact. HIPAA is a perfect example since not all services are HIPAA eligible and therefore not all solutions built in the cloud can become compliant on day one. Let’s dive deeper into what this means.
One way to think about successful compliance is using the equation below:

Successful compliance equation
The first part of the equation focuses on documentation, people, and processes. Formally documented policies govern security and compliance at the organizational level. These policies are enforced using administrative safeguards, or processes and procedures in place to make sure employees comply with said policies.
The second part of the equation is aligned with the architecture of the environment itself, and the implementation of security controls.
Architecting a HIPAA compliant environment can also differ from architecting for another compliance or regulatory framework because, as mentioned before, only a subset of services from the three most common cloud service providers are eligible for compliance. In other words, only some of their products are covered by the Business Associate Agreement, which is the legalese required to document the relationship, roles, and responsibilities of a Business Associate and a Covered Entity. That effectively narrows down the selection of cloud-native services the environment can use to those that are covered by each cloud service provider. The list of services changes all the time so it is important to verify when architecting the environment. Here are some links to the eligible services / covered products of each cloud service provider.
- Amazon Web Services HIPAA Eligible Services
- Microsoft Azure Compliance Offerings
- Google Cloud HIPAA BAA Covered Products
Furthermore, those services have to be configured, implemented, and fine-tuned to reduce risk, protect data, and meet compliance requirements. This technical implementation is the crucial step that determines if the security control is compliant. This is where NIST 800-53 controls can provide a more detailed understanding of how to implement and operationalize the controls.
With the HIPAA equation above in place, an assessment can be performed and documentation formalized to formalize compliance with the regulatory requirements. Once implementation is complete, security and compliance still have to be managed and maintained on an ongoing basis. Automation can help build efficiencies and free employees to focus on important endeavors rather than repetitive tasks.
Keeping all the above in mind, HIPAA compliance can be a deciding factor on which cloud service provider to adopt when designing an environment. Differentiators that might affect this decision include the number of services that are HIPAA compliant, an area where AWS might have an edge. AWS also provides the legalese BAA in its Artifact service, which has to be requested from the other CSPs. Google Cloud might have an edge with regard to implementing some of the security controls since all data is encrypted at rest and when transmitted inside the cloud. In other instances, Azure could be the right choice because of how well the cloud works with what could be existing services, like Active Directory.
Compliance with ScaleSec
HIPAA is a prime example of how an up-front investment in planning, designing, and architecting before implementing a solution could pay substantial dividends in the mid and long term. Like many of its regulatory and compliance counterparts, it focuses on documentation, people, process, and technology; however, technology in this instance can have significant implications if not implemented strategically.
ScaleSec has successfully helped clients navigate these and other complex security and compliance issues. Our compliance team has developed a half-day workshop in which we walk our customers through understanding the compliance requirements and navigating the obstacles and challenges of architecting a HIPAA compliant environment. The workshop can be tailored to the maturity of any organization, starting with the basics or focusing on areas that are problematic for most covered entities.
Following the workshop, ScaleSec works with customers to design and implement comprehensive HIPAA-compliant cloud security solutions, including the launch of security and compliance management programs, cloud platform preparation, and hardened configuration baselines for cloud workloads. To maintain velocity and simplify hiring, the team references well-known standards, tools, and best practices for every layer of the solution.
