Security Implications of Moving to the Cloud
Overview
Making the move into cloud computing brings many security implications for organizations, both positive and negative. In this blog, we will run through some key benefits and concerns that organizations should keep in mind when transitioning to the cloud.
Security Benefits
Cloud computing offers numerous security benefits which mitigate organizational risks. By moving to cloud environments, organizations can reduce security responsibilities and benefit from improved automation and scalability. Below we highlight many of those important benefits.
Shared Responsibility
One of the most significant benefits of embracing cloud is shifting security responsibilities to a third party. Google, Amazon and Microsoft’s clouds all provide details of their shared responsibility models, showing what they take responsibility for with the use of their services. These cloud providers have thousands of security personnel working non-stop to ensure that their environments are secure and security controls are built into their services. The cloud providers’ investments in security are a direct benefit for cloud adoption, as most organizations do not have the resources to invest this amount of attention to security. Cloud users can shift additional security responsibilities to the cloud providers by using Platform as a Service (PaaS) and Software as a Service (SaaS) solutions. This allows customers to focus on securing their applications versus their underlying platforms.
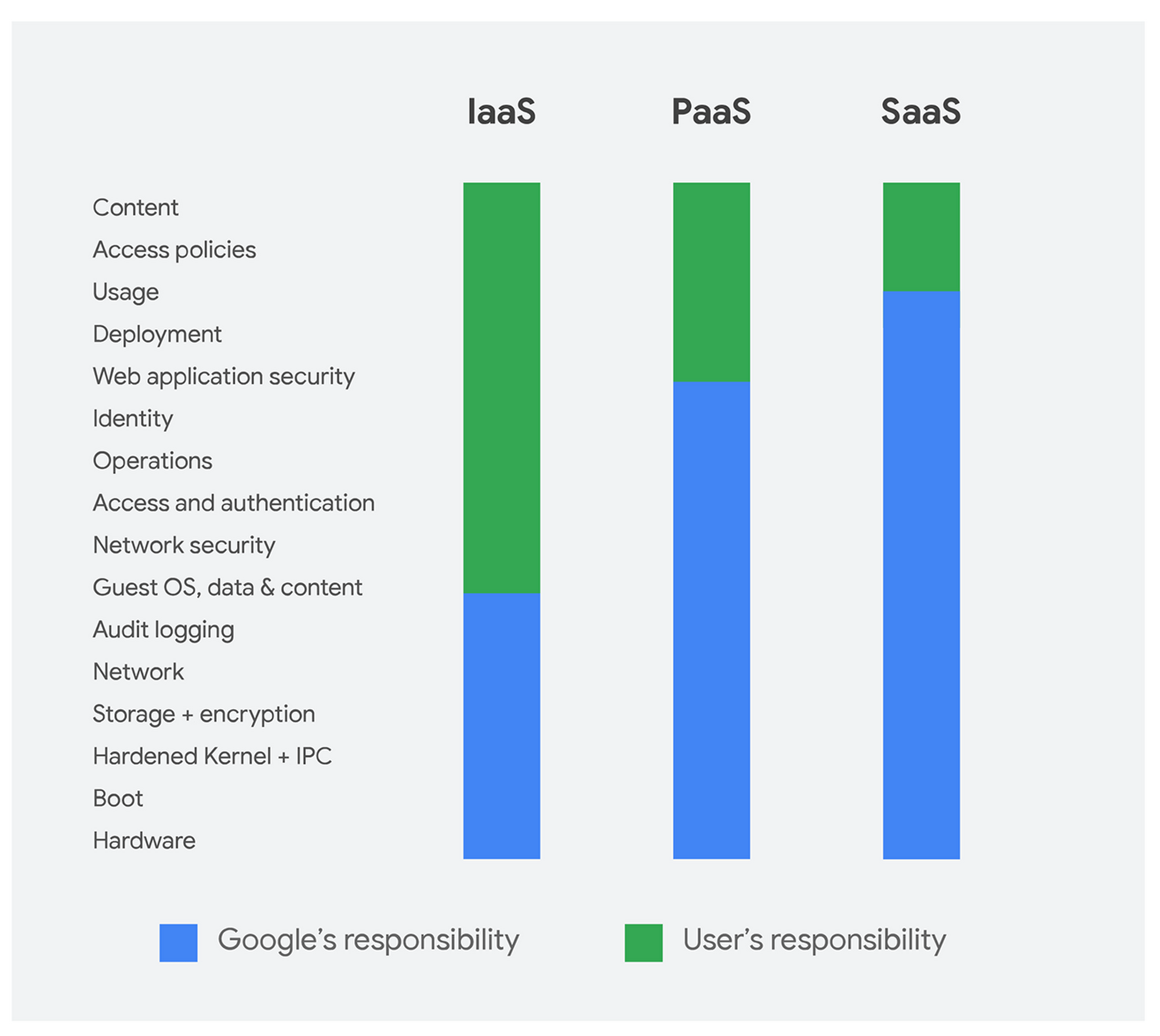
GCP’s shared responsibility matrix
Automation
All major cloud providers have a plethora of security settings and native security tools. Each of these security features can be managed, monitored and tracked via code. By leveraging an Infrastructure as Code (IaC) strategy, an organization can ensure that security controls are baked into new cloud resources or changes to existing ones. Solid IaC practices force all cloud changes through an approved SDLC pipeline with embedded security controls prior to deployment. This allows security and infrastructure teams to ensure that security is part of the build process for all resources.
Additionally, cloud native tools are capable of monitoring your environment for misconfigurations and automating responses, including notifications and remediations. These should be leveraged to reduce the impact time of any misconfigurations, malicious or unintentional.
Scalable Resources
One of cloud computing’s biggest benefits, scalability, also provides numerous security benefits. Most organizations are not capable of dealing with extreme Distributed Denial of Services (DDoS) attacks. Cloud providers have the scale to respond to these. Services such as GCP Cloud Armor, AWS Shield and Azure DDoS Protection allow customers to leverage the provider’s massive bandwidth to absorb and mitigate these massive attacks.

Scalable Resources
The scalability of storage allows security logs to expand exponentially and to be stored for extended time periods. This is useful for legal retention requirements, investigations and rapidly growing environments.
Compliance
Cloud computing generally makes regulatory compliance easier as an organization inherits the compliance of specific services. For example, if an organization is seeking SOC 2 certification, they can inherit the SOC 2 compliance of the cloud resources they are using. Using a compliant cloud service does not automatically make an organization compliant, but it does show that the service already meets the compliance requirements. This reduces the compliance workload considerably for most organizations. AWS, GCP and Azure all list their compliant services online and can provide documentation proving their certification for your auditors.
Key Security Concerns
Moving to cloud computing also introduces security concerns that organizations must be aware of. Below we highlight some of these concerns.
Cloud Sprawl
Cloud computing offers the ability to grow without boundaries. Growth without a solid controls framework can quickly introduce risk to an environment. ScaleSec has helped many organizations with scattered, sporadic controls that have grown organically with little to no structure. Going into a cloud environment without controls in place exposes an entity to additional risk and makes remediation much more difficult as time goes on.
Additionally, many cloud resources are created for a specific purpose and not removed when their functionality is no longer required. This leads to unpatched and vulnerable services/systems running in an environment, potentially leading to an exploit.
Data Exposure
Clouds excel at storing vast amounts of data in an ever-expanding environment. Organizations historically have more data stored than they are aware of, generally stored in disparate locations (storage buckets, virtual drives, databases, etc.) A large percentage of companies do well at backing up data, but many fail to maintain data retention and deletion procedures. This leads to large amounts of undocumented data being stored throughout the cloud, potentially remaining forever. Protecting this vast amount of data becomes difficult without proper security controls used throughout the environment. There are numerous examples of data breaches due to data being exposed unintentionally by organizations.

Read more on Data Retention from ScaleSec
Identity Management
All cloud users require identification and authentication to access cloud environments. Everything in cloud computing is an API and most APIs require authentication. Third-parties, applications and services access cloud resources and require authentication services. With all of these identities in use, the management of them becomes complex. Ensuring that the principle of least privilege is followed becomes more difficult to track due to this. Putting a solid identity management system in place is essential to security in the cloud, but the complexity of these environments can lead to unintended consequences. Numerous breaches have been reported due to identities being unintentionally exposed and misused in cloud environments.
Read ScaleSec's Cloud-First API Security article
Read about AWS IAM on ScaleSec
Conclusion
Hosting an organization’s information systems within the cloud reduces many security risks associated with infrastructure, such as physical security, but does not remove all security responsibilities. Most organizations will see security benefits from moving to the cloud, but they must address cloud specific security concerns such as data exposure, identity management and unstructured sprawl.
Reach out to us at ScaleSec to see how we can assist with implementing your cloud environments securely - this is what we love to do.