Security Protection Using NIST CSF
What is NIST CSF?
The National Institute of Standards in Technology CyberSecurity Framework (NIST CSF) was created to help organizations assess and manage risk in their environments. NIST CSF guidelines provide curated controls to meet compliance and security requirements.
NIST CSF allows organizations to document existing security controls and identify gaps. By following CSF guidelines, organizations can reduce risk now and in the future.
The Spirit of CSF:
NIST CSF doesn’t require an organization to meet every guideline. An organization will decide what guidelines apply to their specific resources and requirements.
For example, here is a non-applicable guideline:
If an organization does not have mobile-specific code (e.g. phone app), mobile code scanning is not applicable. (DE.CM-5)
The spirit of NIST CSF is to guide an organization to a robust security program, not to adhere strictly to guidelines in a way that won’t prove useful.
NIST Policies
NIST has created various compliance standards that try to respond to a changing technology landscape.
NIST provides over 1,300 reference materials for consumption. NIST CSF is a consolidated collection of controls taken from NIST SP 800-53 rev 5. While 800-53 is a great standard to work toward, its depth can be daunting for some organizations.
NIST CSF provides comprehensive security guidelines while remaining digestible, especially for those not ready to meet the more stringent NIST 800-53 requirements.
Realized Benefits:
Aligning to NIST CSF is voluntary, but it can provide many benefits, such as:
- Outlining understandable security best-practices
- Stronger understanding of current security risks and improvement opportunities
- Clearer strategic direction
- More effective budget planning
- Internal & External risk audits can be simplified
- Easily transferable controls into other compliance frameworks such as SOC 2, PCI, and ISO 27001
- Improved communication with stakeholders
ScaleSec NIST CSF Security Program Launch
ScaleSec offers a NIST CSF Security Program Launch to assist organizations with implementing CSF. ScaleSec’s CSF offering is customized and flexible, and it’s designed to meet an individual organization’s risk management needs.
ScaleSec security experts take an organization through the CSF Launch process. ScaleSec will develop a tailored action plan and roadmap for an organization. It’s a right-sized approach to implementing NIST CSF.
NIST CSF
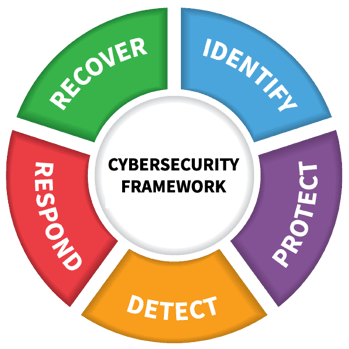
NIST CyberSecurity Framework
The NIST Cybersecurity Framework consists of 5 core functions:
Core:1
- Identify
- Protect
- Detect
- Respond
- Recover
Each function has varying amounts of guidelines.
Examples:
Identify:
- Identify assets in the organization
- Understand vulnerabilities to known assets
- Identify a risk management strategy
Protect:
- Implement an approved IAM program
- Manage processes and procedures for systems
- Ensure adequate patching and maintenance is in place
Detect:
- Understand normal baseline activities and identify anomalies through monitoring
Respond:
- Implement mitigations in response to an event
- Communicate to internal and external stakeholders during an event
Reimages:
- Ensure a program is in place to restore systems after an event
- Implement lessons learned and improvements in response to an event
Implementation Tiers:2
With NIST CSF, an organization can examine each control to determine what level of conformance is being achieved. The level of conformance in the current state can be compared to that of the desired state. These levels are known as tiers.
There are 4 tiers that an organization can align to under CSF:
- Tier 1: Partial — Informal, nonexistent or unsystematic risk management methods
- Tier 2: Risk Informed — Partial implementation or unfinished risk management processes
- Tier 3: Repeatable — Formal and structured policies. Procedures follow a robust risk management program
- Tier 4: Adaptive — Responsive risk management programs that are continuously adapted and improved
Many organizations will have some of their controls fall under Tier 2, with Tier 3 being an attainable goal. It is not necessary, or advisable, to bring every control to Tier 4. NIST suggests Tier 4 remains reserved for areas critical to a line of business. A cost-benefit analysis should occur when aiming for Tier 4.
Profiles:
An organization consists of many business units. Some business units will have specific risk requirements from others. As NIST CSF has over 100 controls, it’s natural that not every control will apply to every business unit. NIST CSF addresses this by utilizing Profiles.
An organization will decide what areas are important to capture in any one profile. The profile is then compared against an organization’s risk tolerance and requirements. Using profiles, CSF can be tailored to a specific organization’s needs.
CSF profiles serve as a snapshot in time of an organization’s security posture. Profiles allow a better understanding of the current state of controls. Profiles also serve as the guide and roadmap for obtaining the next CSF Tier.
It is important to understand that a profile is not meant to be rigid. A new profile version should be created any time capabilities or requirements change.
Starting with NIST CSF
NIST provides a free spreadsheet that allows an organization to understand each functional area. A completed sheet will guide CSF prioritization in an organization.
ScaleSec finds some organizations view the CSF process as disconcerting. CSF will highlight deficiencies in a current security program; therefore, it is important to not overcomplicate the process. NIST CSF serves as a guide to security improvement, but it doesn’t dictate hard requirements or specific technology. An organization should tailor CSF to the specific culture and resources within.
While an organization can keep the NIST CSF alignment process entirely in-house, many find it’s not optimal to do so. In most cases, internal IT teams have designed current processes and, for some, changing processes can be a challenge.
ScaleSec can help an organization identify CSF priorities relative to specific requirements. ScaleSec will partner with a client to find the path to CSF alignment in an optimal way.
CSF In The Cloud
Cloud platforms provide native technologies and services that help organizations meet CSF guidelines. These technologies and services can help simplify the engineering workload that organizations shoulder as part of implementing CSF.
AWS has several cloud native services, such as GuardDuty and Macie, that can be used to meet CSF control guidelines. Similar cloud native services exist on GCP and Azure.
An example of meeting CSF controls in GCP:
Applying NIST Cybersecurity Framework to GCP Implementations:3
| Core Function | Control | GCP Technology | GCP Technology Description |
|---|---|---|---|
| Identify | ID.AM-1 - Devices & Systems are inventoried | Cloud Asset Inventory | Cloud Asset Inventory provides inventory services based on a time series database. |
| Identify | ID.AM-6: Roles and responsibilities are established | Cloud IAM | Define access roles & permissions |
| Protect | PR.DS-1: Data-At-Rest is Protected | Google Encryption at Rest | All data in Google is encrypted at rest by default using envelope encryption |
| Protect | PR.DS-5: Protections against data leaks are implemented | Cloud Data Loss Prevention | Automatically discover, classify, and redact sensitive data |
| Detect | DE.CM-1: The network is monitored to detect potential cybersecurity events | Cloud Armor | Protect infrastructure and web applications from Distributed Denial of Service (DDoS) attacks |
| Detect | DE.DP-4: Event detection information is communicated | Cloud Security Command Center (CSCC) | Security and risk management platform for Google Cloud, with real-time notifications. |
| Respond | RS.RP-1: Response plan is executed during or after an incident | Incident Response Management | Leverage IRM with Monitoring to identify, manage, investigate, and resolve incidents |
| Respond | RS.CO-5: Voluntary information sharing occurs with external stakeholders to achieve broader cybersecurity situational awareness | Identity Platform | Identity Platform is a customer identity and access management (CIAM) platform. Can be used to add identity to external facing apps. |
| Recover | RC.IM-2: Recovery strategies are updated | Google Cloud Disaster Recovery Planning Guide | Build a disaster recovery architecture and plan for data and applications in Google Cloud |
| Recover | RC.CO-3: Recovery activities are communicated to internal and external stakeholders as well as executive and management teams | Contact Center AI | Combine the best of Google AI with your customer contact center software to improve customer experience and operational efficiency. |
Final Thoughts
Security in any organization can be complex. There are many people, processes, and technologies all working toward their specific goals. Because of this natural complexity, an organization needs a clear security roadmap that all can understand.
NIST CSF aligns an organization to industry guidelines and standards. CSF benefits are anchored by a clear understanding of an organization’s security processes and requirements.