Cloud-Native Ransomware Protection in GCP
Introduction
Organizations that leverage cloud services have a requirement to protect the data they store and safeguard the systems which store and process the data. This can be a daunting task as technology evolves and resources become limited. In addition, organizations need to remain vigilant as threat actors attempt to gain unauthorized access to sensitive data.
The Cybersecurity and Infrastructure Security Agency (CISA) defines ransomware as
“an ever-evolving form of malware designed to encrypt files on a device, rendering them unusable. Malicious actors then demand ransom in exchange for decryption. Ransomware actors often target and threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid.”
Cybersecurity and Infrastructure Security Agency (CISA)
Ransomware attacks can lead to any one of the following outcomes or a combination thereof:
- Inability to conduct business
- Inability to manage systems for an extended period of time
- Data becomes exposed publicly
- Applications are unable to run due to access restrictions on the data
- Data becomes encrypted, corrupted, or deleted
- Tarnished reputation
- Loss of customer trust
- Loss of business
This document will highlight how organizations can prevent ransomware attacks by taking a defense-in-depth approach. The security controls you deploy should align with established frameworks like the NIST Cyber Security Framework (CSF).
Defense-in-depth approach
Where do I start?
Organizations should perform a detailed risk analysis to determine their organization’s exposure to ransomware. The research would provide insight into the impact of an attack. Ransomware prevention is more than a business continuity effort. It requires that security and disaster recovery efforts are reviewed simultaneously, as focusing on one will not prevent the attack.
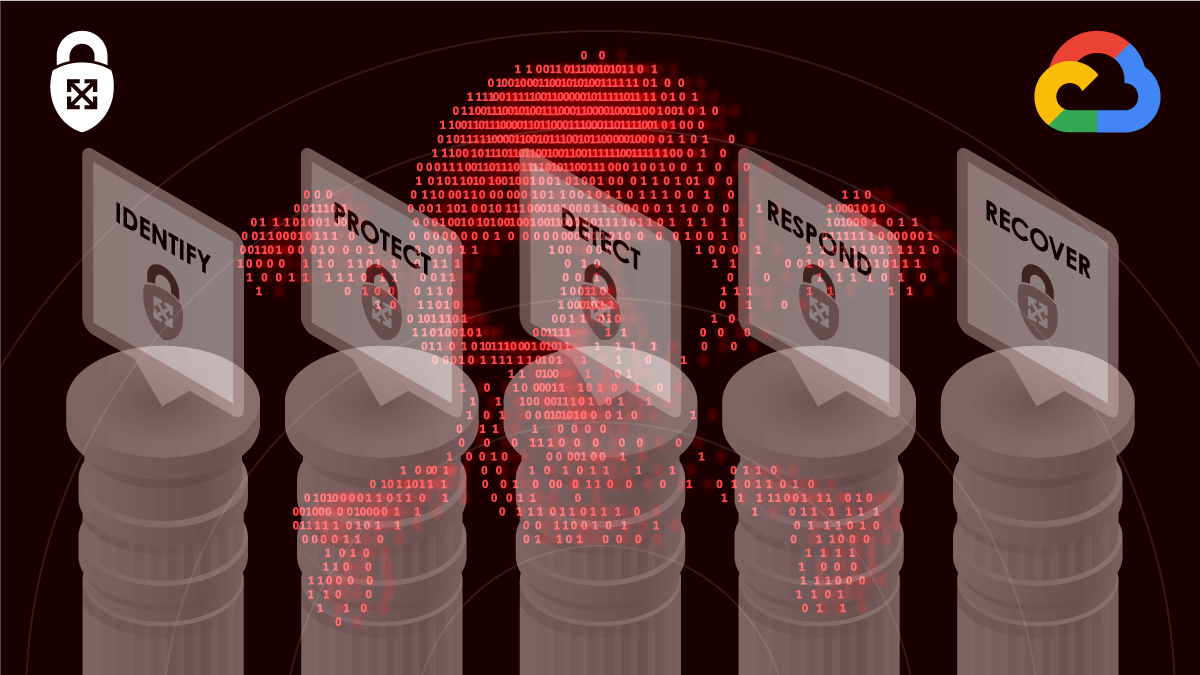
Aligning protection activities with the five pillars of the NIST CSF is a great place to start. Those pillars include Identify, Protect, Detect, Response, and Recover. Organizations should understand the controls available and identify gaps. In the following few sections, we will review what GCP capabilities exist to help you deploy controls that align with the pillars of the NIST CSF.

The five pillars of the NIST CSF
Identify
In the Identify pillar, organizations need to understand managing risks to systems, data, assets, people & capabilities.
In Google Cloud Platform (GCP), Cloud Asset Inventory (CAI) provides complete visibility into all the cloud assets in a centralized location. With CAI, you can continuously monitor the number of assets that get deployed within your environment. CAI allows organizations to analyze and audit their asset inventory to meet security and compliance requirements. Knowing what assets exist within your organization is critical in applying the appropriate security controls to assets.
In addition to CAI, organizations can also leverage Cloud DLP to gain visibility when sensitive data is stored and processed. Additionally, Cloud DLP supports automated sensitive data discovery and classification and secure data handling. Knowing the various data classifications in your environment is just as important as knowing what assets exist. Identifying the minimal amount of data to conduct business helps reduce the blast radius of an attack.
Protect
In the protection pillar, the goal is to define appropriate safeguards to ensure critical infrastructure service delivery.
Tools like resource manager allow organizations to centrally control organization’s resources, manage IAM across their organization and track and manage projects. Resource manager lets organizations separate resources at the project level using folders. Since resource manager is a feature of IAM, it goes without saying that IAM is an integral part of your protection strategy against ransomware.
IAM allows organizations to manage access control by defining who (identity) has what access (role) for which resource. IAM will enable you to enforce the principle of least privilege through the use of custom roles or pre-defined roles within a GCP environment. IAM also has conditions applicable to IAM policies for additional security on a resource. In addition, IAM products like BeyondCorp Enterprise support a zero-trust architecture which is great for protecting data and assets.
Zero Trust relies on WHO you are and WHAT you are using to determine access. GCP offers default encryption for all data that enters an environment. Still, for more advanced organizations, Customer Managed Encryption Keys or Customer Supplied Encryption Keys are available for protecting your data from malicious actors.
Protecting the software supply chain involves shifting security left and incorporating security controls early in a CI/CD process. Products like Binary Authorization require images to be signed by trusted authorities during the development process and then enforce signature validation when deploying. The artifacts used to build your images can be stored in products like Artifact Registry.Artifact registry allows you to perform vulnerability scans on your artifacts to ensure no vulnerabilities are deployed during build time. Services like VPC Service Controls can be used to deploy a perimeter around your environment to help prevent data exfiltration.
In addition to the services listed, GCP also offers VM Manager to help apply OS patches across your fleet of Compute Instances that you have running in your environment. Utilizing these cloud-native services will keep your data safe from threat actors.
Detect & Respond
In the detect & respond pillars, the goal is to define activities that will identify the occurrence of an event & enable timely discovery of these events.
Cloud Logging & Monitoring serve many different functions in an environment architecture. They facilitate detection and response capabilities for data integrity events when set up correctly. Building observability into your cloud environment gives you the ability to spot and stop malicious activity as early as possible to prevent business from stopping.
Security Command Center (SCC) and Chronicle are great cloud-native products that support a preventative, detective, and responsive measure to protect against ransomware.
SCC provides vulnerability and threat reporting capabilities by evaluating the security of your environment along with the data attack surface. SCC can also identify misconfiguration, vulnerabilities, and threats in your environment to help mitigate and remediate risks.
Chronicle is a security telemetry platform built on top of Google infrastructure. Chronicle can ingest, analyze and search through massive amounts of security and network data collected from internal log data like network alerts, DNS, EDR, and other valuable logs.
With the integration between Chronicle and SCC, users can now use Chronicle to perform a detailed investigation on events surfaced through SCC’s Event Threat Detection service. Chronicle automatically parses log data and normalizes it to enable capabilities like Indicators of Compromise matching, threat hunting, and investigations across all the data sources ingested by Chronicle. With this level of data insight, security teams can detect and respond to potential ransomware threats.
Recover
With the rise in ransomware, having a robust recovery strategy is a must. Google Cloud created a Disaster Recovery Planning Guide which outlines different considerations and patterns that can be incorporated into your backup and recovery strategy.
Leveraging the DR planning guide practices will ensure that you can recover data regardless of how it was made inaccessible.
Some of the building blocks discussed in the DR Planning guide include creating architectures that leverage services like Compute Engine, Cloud Storage, File Store, Cloud Load Balancing, Traffic Director, Cloud DNS, and Cloud Monitoring. Each of these products can be leveraged to make a resilient DR strategy that considers different recovery point objectives (RPO) and recovery time objectives (RTO).
In addition, Google Cloud has built-in recovery capabilities in some of the database solutions, such as BigTable managed backup solution that lets you save a copy of a table’s schema and data, then restore from the backup to a new table later. Depending on your recovery point objective (RPO) and recovery time objective (RTO) requirements, implementing a resilient DR strategy can be costly, depending on the level of complexity applied to the strategy.
Conclusion
The fight against ransomware will never stop; organizations must be vigilant in applying security measures to protect data and maintain a resilient security posture. A layered security approach must be taken to identify, protect, detect, respond and recover from threats. Many of the tools outlined in this article should be used to protect against and recover from ransomware attacks.
