The symposium was held on November 2, 2023 at the Joan B. Kroc Center for Peace and Justice at USD.
Risky Tales and Ransomware Fables
from the CyberTrenches
The Cyber Law and Risk Symposium hosted at University of San Diego was packed with presentations long and short, clearly designed to ensure every attendee got their money’s worth out of the day. Big shout out to Justine Phillips, Mark Castellano and their whole program team for a terrific day of learning and networking.
Here are my synopses, complete with links for further exploration, that I hope you can learn from and apply to your world.
Note: The links amplify the messages shared during the symposium, and are from own my research after the fact.
The overarching theme of the day was Resilience by Design, delivered via stories and fairy tale metaphors. The audience of attorneys, regulators, and law enforcement and cybersecurity professionals was a fantastic cross section of leaders, all of whom have a vital role to play in the security of clients, businesses, critical infrastructure and more.
David Hirsch, Chief of the CryptoAssets and Cyber Unit, SEC Division of Enforcement kicked off the morning with a "fireside chat."

David Hirsch and Cathy Mulrow-Peattie talk about SEC and disclosures.
David underscored a number of key takeaways during his presentation. When dealing with breach notifications, a company needs to share what investors need to know in order to make investment decisions. They must use a principles-based approach to disclose should an incident occur. There's no prescriptive checklist; documentation will be key to demonstrate intent. When companies do disclose, they must explain the processes in a way that can be understood by investors, avoiding acronyms and industry jargon. Essentially, you must do what your cyber security program says you do. See more here.
Katherine McCarron, Chief of Staff and Attorney, Division of Privacy And Identity Protection, Bureau Of Consumer Protection, led the discussion for the FTC.
Katherine did a thorough job of walking the audience through the new FTC Safeguards Rule provision, including what kinds of companies the Rule affects, what the Rule requires companies to do, and what a reasonable infosec program looks like, at least to the FTC. Recommend reading for more details around what Katherine shared.

UCSD Professor Stefan Savage shared engaging stories about cybercrime demonetization efforts he has led.
Stefan Savage, Professor of Computer, Science, and Engineering at UC San Diego, entertained us with stories around cybercrime demonetization efforts and civil interventions. It is clear that law enforcement can not keep up with the many ways cybercrime is occurring, so how can we as leaders of companies make life harder for the threat actors? While all the stories were interesting, and you can find many here, my main takeaway was to consider being kind to the person that may be trying to scam you, this insofar as they are likely from another country, paid very little/poverty wages if anything, and they may even be indentured. It never occurred to me that this form of slavery would exist and it opened my eyes.
The next presentation with Jennifer Martin, Jeff Macko, CISSP, and Sean Poris focused on Securing The Supply Chain And Vendor Management. The panel spent 35 minutes sharing how Executive Order 14028, while it is for software sold to the government, will eventually also influence the way software for commercial entities is built as well. Given that the audience was made up of both more technical and less technical professionals, the panel walked through the definition of software, vulnerability management, the SDLC, and the SBOM. This followed with a lively discussion around how granular the SBOMs must be to be useful. Finally, the experts advised companies to use centralized code repositories, including the open source used in the build, pick just one language to build in, use a software composition analysis tool, and bring in an outside perspective to affirm your approach.

Marc discussed how he helps companies pay ransoms in crypto (photo credit CNBC)
In his lightning talk, Marc Jason Grens, Cofounder and President of Digital Mint, shared three blockchain crypto forensics stories that showed how simple the basic blockchain actor can be: the need to use a clean wallet (vice a used one), and the challenge of latency when delivering coin to the bad guys in a volatile market (thief kept saying that ransom was coming up short, much to the chagrin of the insurance provider who was making the iterative payments). Marc closed with the story of a bad actor with a big heart who extorted a nonprofit that helped kids. The nonprofit paid their ransom then found a few days later, the thief had apologized and had returned the money. LOL. See this video for more.
Closing out the first half of the day, Clayton Romans (CISA), Todd Hemmen (FBI), Nick Arico (FBI), and Justine Phillips (moderator) led a lively panel around Federal Cyber Reporting Obligations as well as the actual cyber requirements around companies designated as part of Critical Infrastructure. Also on deck was conversation around Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA) and how the requirements for companies to report cyber attacks are changing. The panel talked at length about the voluntary sharing of information about cyber incidents across FBI and CISA. Additional resources included here and here.
Our first post-lunch speaker was Palo Alto Networks Senior VP for Unit 42, Wendi Whitmore, who had just flown back from the third White House-sponsored International Counter Ransomware Initiative (CRI) in Washington, D.C. Wendi’s lightning talk about Ransomware Variants and AI expounded on two trends in ransomware. First, the move towards extortion, and second, how attackers are making it personal. You might want to watch the video in this article for more.
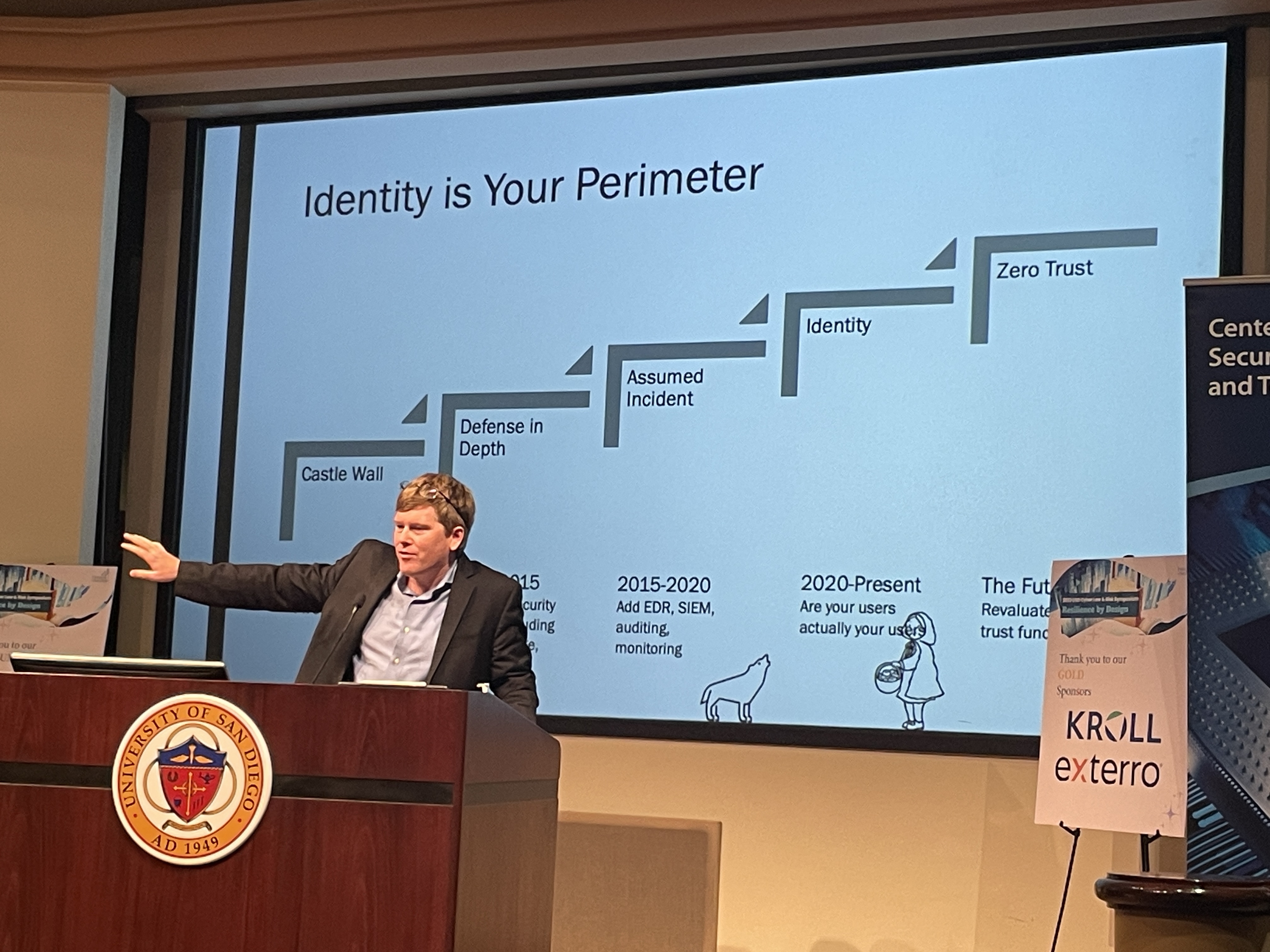
Pierson Clair made us all question IDENTITY and how we prove it to access technology.
Pierson Clair, Professor, USC School of Engineering, delivered a witty deck that was a deep dive on MFA: what really IS identity, and how can we address MFA fatigue so we can stay as secure as possible? The audience nodded as we all appreciated how hard it was to get basic end users (our parents, for example) to use MFA, as well as the privacy concerns (and regulations limiting) biometric validation of identity. The presentation ended around a lively discussion of limiting session tokens or using yubikeys to balance the need for security and authentication.

This mock trial had a real look and feel, along with fun, fictional parody.
Putting Your CISO on the Stand: With eerie and sarcastic similarities to the ongoing SEC investigations in the news, the Honorable Mitch Dembin, US Magistrate Judge, and two fine attorneys from Baker & McKensie LLP, Cyrus Vance and Justine Phillips, held a mock trial to determine the fate of vCISO ("v" stands for volunteer or victim?) Matt Stamper, CIPP/US, CISA, CISM, CRISC, CDPSE, QTE. This one hour, engaging session allowed the audience to observe the intricacies of the courtroom process as a vCISO tries to defend his make-believe product that caused the death of the Princess Sleeping Beauty. It was good fun, and the audience was able to gain insights into the process of determining fault around products, ransomware and mandatory disclosures.

Obtaining cyber liability insurance is more challenging by the day, as more companies are dealing with ransomeware demands.
Monique Ferraro, Sadia Mirza, CIPP/US, CIPM and Violet Sullivan, CIPP US discussed the challenge of finding cyber insurance as a company in the ever changing landscape of current business. While once cyber was covered under commercial general liability, now it is its own stand alone policy. Cyber insurance covers the most prominent cyber risks, which are privacy risk, security risk, operational risk, and service risk. With about four companies reporting per day that they are under cyber attack, cyber insurance carriers are now facing unprecedented losses under these policies. This has resulted in a difficult market that includes higher prices, more scrutinized review of security controls, and/or limitations on coverage in the form of co-insurance or sub-limits for ransomware. Of note is that having cyber insurance does not just cover the issues associated with the insurance itself, but having it also allows you to have one place to call to start all the important processes when you are under attack.
Later in the afternoon, tasked with sharing how he is telling and writing his own Cyber Story, Patrick Burns, IR and BD Manager at Sentinel One, delivered an eloquent lightning talk that combined his Masters in Fine Arts with his love for cybersecurity. He shared a thoughtful parable about the humanity of cybersecurity and how we can leverage that to all make ourselves better practitioners.
The last talk of the day before participants were treated to happy hour and a stunning sunset, was focused on critical policy and compliance considerations arising from 2023 regulatory changes. Cathy Mulrow-Peattie and Steven Ward discussed how regulatory changes could impact organizations' cybersecurity governance, processes, and risks, from a policy, risk and regulatory lens. Further, from the September 8, 2023 draft California Cybersecurity Audit Regulations, all businesses that derive 50% of their revenue from selling or sharing personal information would be required to conduct cybersecurity audits. Additionally, cybersecurity audits would be required for businesses meeting certain (to-be-determined) thresholds. Homogenizing multi-state and Federal requirements will be an ongoing issue for companies looking to stay compliant. More on this here.
Without a doubt, I highly recommend this intimate and informative symposium for all professionals whose work revolves around keeping companies safe from bad actors. We all have a role to play in thwarting the enemies from nations states as well as criminal elements. Hold November 7, 2024 in your calendar for next year's Symposium.
