Two of our favorite NIST publications are in the news, being mentioned by both SolarWinds and the SEC in their recent legal battle. Across online forums and social media, there seems to be some general confusion about the purpose of these pubs. In this post I'll describe the NIST Cybersecurity Framework and NIST Special Publication 800-53, and how they can be used together.
tl;dr - CSF tells security teams WHAT to do; 800-53 tells us HOW to do it.
In its filing against SolarWinds/Brown[1], the SEC states: "SolarWinds identified having a 'program/practice in place' for only 21 of the 325—or 6%—of NIST 800-53 controls."
SolarWinds responded[2] that this "... has nothing to do with whether it followed the NIST CSF. The SEC is mixing apples and oranges, underscoring its lack of cybersecurity expertise." Well, whether they are using apples or oranges, 6% is a scary score any way you slice the fruit. A score this low is an indicator that an organization doesn't have fundamental security controls in place.
As even NIST notes, "the variety of ways in which the Framework can be used by an organization means that phrases like 'compliance with the Framework' can be confusing and mean something very different to various stakeholders."
And here we all are! Confused. What does it all mean? Let's start with the basics.
What is NIST?
The National Institute of Standards and Technology (NIST) was founded in 1901 and is now part of the U.S. Department of Commerce. NIST's scope includes "the smallest of technologies to the largest and most complex of human-made creations — from nanoscale devices so tiny that tens of thousands can fit on the end of a single human hair up to earthquake-resistant skyscrapers and global communication networks."
NIST is one of the organizations typically tasked with improving cybersecurity for the United States, via Executive Orders across education, critical infrastructure, among other mandates[3].
So NIST has some of the Nation's smartest people working on some of the most complicated technology topics. Given the massive breadth and depth of the subject matter NIST handles, I have learned to be wary of anyone claiming to be a "NIST expert" who doesn't actually work at NIST.
What is NIST Special Publication 800-53?
NIST SP 800-53[4] is a popular industry standard for security and privacy controls. The 463-page publication includes a comprehensive controls catalog you can use to secure information systems. It includes guidance on implementing the controls, measuring their effectiveness, meeting risk objectives, and process improvement. It also includes Baselines to tailor the controls to the needs of specific organizations and systems.
NIST SP 800-53 defines the security and privacy standards referenced by many other NIST publications, including:
- NIST SP 800-66, An Introductory Resource Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule
- NIST SP 800-171, Protecting Controlled Unclassified Information in the Cloud
- NIST SP 800-161, Cybersecurity Supply Chain Risk Management (C-SCRM)
- NIST SP 800-181, Cybersecurity Considerations for Software Acquisition
- NIST SP 800-204, Security Strategies for Microservices-based Application Systems
- …and many more…
NIST SP 800-53 is also commonly referenced by other standards organizations like the International Organization for Standardization.
What is the NIST Cybersecurity Framework?
NIST CSF[5] is a voluntary framework that provides guidance on how to use existing standards to improve your cybersecurity program. It offers 55 pages of tools, methodologies, and guidance to measure and improve your cybersecurity program, considering your business and your risk appetite. It was originally created in response to the Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” in 2013 for critical infrastructure owners and operators.
Defines Outcomes Mapped to Existing Controls
NIST CSF is not a standard, and it doesn't contain controls. It defines 108 outcomes categorized into five high-level security functions: Identify, Protect, Detect, Respond, and Recover. Each outcome includes mappings to existing standards, guidelines, and practices. You are free to choose from any standards they prefer such as COBIT, CIS, ANSI, ISO, AICPA, or … NIST SP 800-53!
Includes Tools to Improve Your Security Program
To improve your program over time, NIST CSF offers two Profiles you can use to assess and improve your program by rating the current state today –the "Current Profile"– versus the desired state–the "Target Profile." Each of the 108 outcomes gets two ratings for the Current Profile and Target Profile.
To rate the Profiles, NIST CSF uses "Implementation Tiers" to qualitatively rate the degree of rigor and sophistication for each outcome from the lowest rating of 1 "Partial" to the highest rating of 4 "Adaptive". For example, if your team didn't enable logging on your VPN, you should expect a low rating for the outcome that requires logging (PR.PT-1).
After you assign ratings for the Current Profile and Target Profile, you can then create an improvement plan that prioritizes your limited security investments to treat risks where you have the greatest gaps. This is how NIST CSF is useful for not only critical infrastructure providers, but large enterprises, government agencies, and even startups. It helps you spend limited resources where you will best reduce your risk. This is the beauty of NIST CSF, and why you would use it with NIST SP 800-53 as a reference.
It's important to note that a Tier 4 rating should be reserved for only the most critical outcomes. Achieving a Tier 4 rating comes with substantial expense to implement controls and processes. Setting the Target Profile for every outcome to Tier 4 would be financially unfeasible and technically unnecessary for most organizations.
How does the CSF relate to 800-53?
NIST CSF is often used by decision makers to measure and improve a security program over time. NIST SP 800-53 is usually a reference used by practitioners and auditors to understand the implementation of a system and how well it meets requirements. If NIST CSF represents the blueprints for a house, NIST SP 800-53 are the building code specifications.
In its rebuttal to the November 2023 SEC filing, SolarWinds wrote, "The SEC says that SolarWinds falsely claimed to follow the NIST Cybersecurity Framework (CSF). However, the supposed evidence for this claim is mainly a preliminary self-assessment from 2019 as to whether SolarWinds met an entirely different set of standards—those in NIST Special Publication (SP) 800-53..."
So, are NIST CSF and NIST SP 800-53 entirely different sets of standards? No, they are complementary resources that can be used together. Only NIST SP 800-53 is a standard. NIST SP 800-53 includes controls. CSF provides defined outcomes that can be met using existing controls. Depending on the standard selected, an outcome might map to more than one control, as shown in the following diagram.
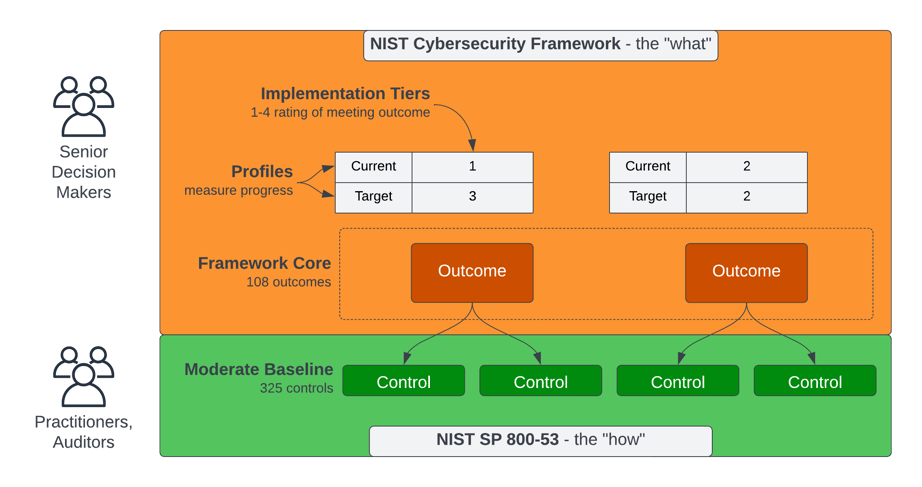
How NIST CSF and NIST SP 800-53 can be used together
Let's Follow Through an Example
Consider how these two frameworks might approach the requirement to protect the integrity of software a company creates. NIST CSF includes a related outcome:
|
Integrity checking mechanisms are used to verify software, firmware, and information integrity |
NIST CSF outcome PR.DS-6
The outcome is the "what" - the thing we need to do to protect our software. Then, NIST SP 800-53 is a standard that defines the "how" which is the technical implementation requirement that meets the desired outcome.
|
The information system implements cryptographic mechanisms to detect unauthorized changes to software, firmware, and information. |
NIST SP 800-53 control SI-7
Most of the NIST CSF outcomes map cleanly to relevant SP 800-53 controls. The CSF publication includes this mapping in Appendix A. The diagram shows how the NIST CSF outcomes (shown in orange) map to NIST SP 800–53 controls (shown in apple green). As you can see, the two documents largely address the same concepts. In fact, only a few NIST CSF outcomes[6] do not map well to NIST SP 800-53.
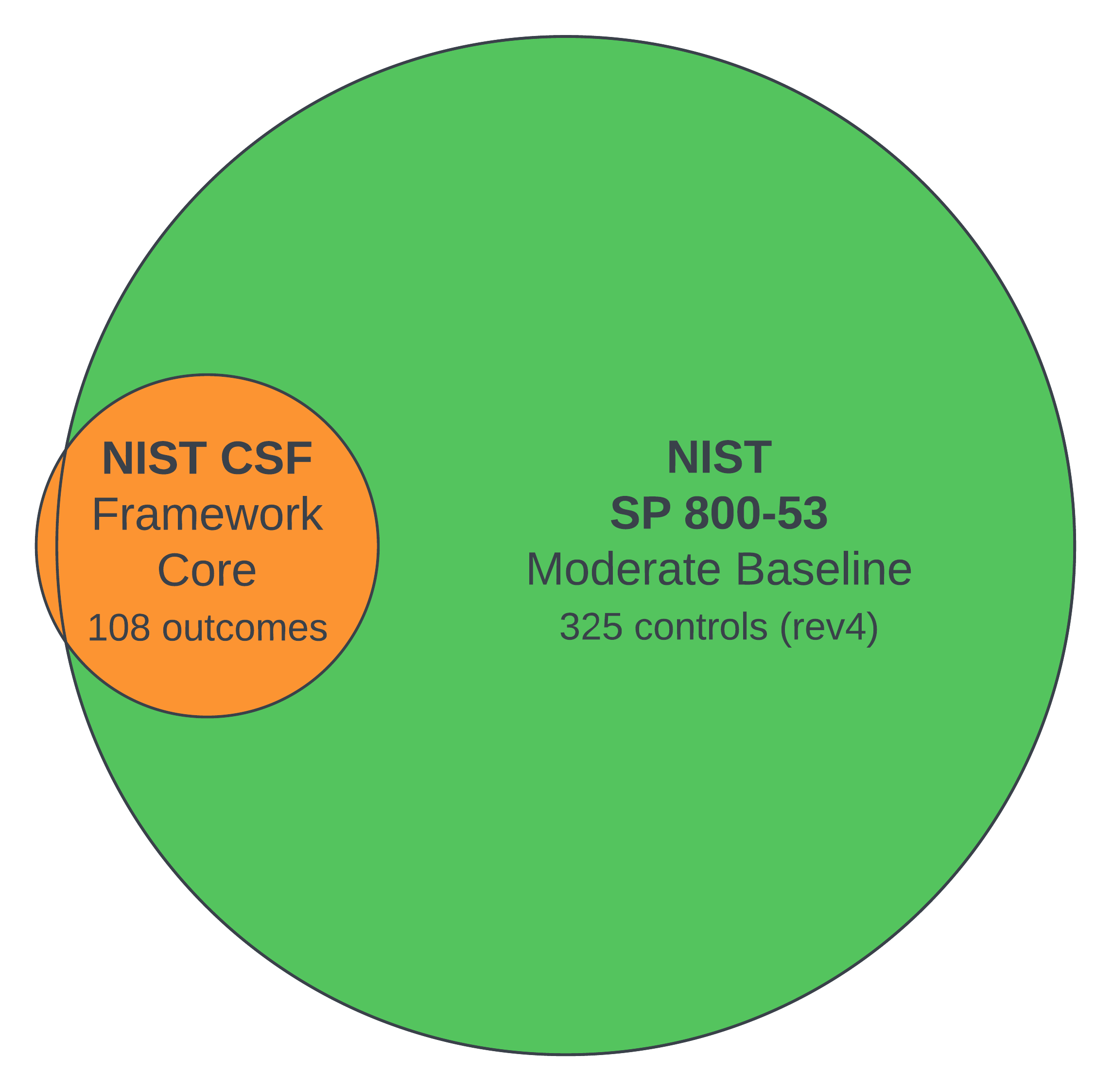
How CSF outcomes map to 800-53 controls
Conclusion
In this post we explained the purpose of the NIST Cybersecurity Framework and NIST Special Publication 800-53. Together these publications can help any organization build and improve a security program.
Perhaps some of the confusion about NIST CSF stems from its flexibility. It is designed to be scalable and modular to fit organizations of all sizes and shapes. There are many decisions to make like "Which existing standards should we use?" and "How do we evaluate the Implementation Tier rating for our Current Profile?" We recommend working with a knowledgeable NIST consultant as a guide through the setup process.
At ScaleSec we've used NIST CSF successfully with regional banks, payment processors, hospitals, retailers, and fintech startups. Customers tell us that NIST CSF is helpful in up-leveling the conversation with executives to communicate risks and justify security budgets. They also appreciate how NIST CSF focuses on improving the security program over time, which is helpful in meeting the bar defined by NIST SP 800-53.
While NIST publications are comprehensive and powerful tools, the deployment and integration processes can be confusing. If you're struggling to fit these puzzle pieces together, reach out for guidance to build a robust and manageable security program that can be improved over time.
[1] https://www.sec.gov/files/litigation/complaints/2023/comp-pr2023-227.pdf
[2] https://orangematter.solarwinds.com/2023/11/08/setting-the-record-straight-on-the-sec-and-sunburst/
[3] See recent relevant Executive Orders: 14096, 14056, 14036, 14028, 13859
[4] Revision 5 is current, though revision 4 would have been the version in use during 2018-2021.
[5] The current version is version 1.1 is current, and version 2.0 is in draft.
[6] NIST CSF outcomes RC.CO-1 and RC.CO-2 relate to preparing public relations to manage an organization's reputation after an incident.
