
Creating Your Cloud Migration Security Plan: How & Why?
- How Cloud Security Enables Your Migration
How Cloud Security Enables Your Migration
Research indicates that security is the top challenge for IT decision-makers when moving to the cloud. Developing a security plan before your migration begins can help your organization tackle this challenge, prevent stalled migrations, and make the transition easier.
Cloud security is different from on-premise security. Concepts may be similar, but many unique attack vectors exist and specialized tools are available to combat them effectively. These differences must be understood and planned for from the very beginning as organizations move to the cloud.
What Constitutes a Successful Cloud Migration?
There are a variety of key performance indicators (KPIs) to gauge your success when migrating to the cloud. These KPIs should align with your business objectives and may include cost and time savings, financial metrics, performance, and user experience. Implementing security from the onset can help with all these, but let’s focus on a few security-specific measurements.
- Can your engineers innovate autonomously while following security requirements?
- Are you in compliance with applicable laws and regulations?
- Can you automatically detect and respond to misconfigurations?
- Are there guardrails in place to prevent misconfigurations from happening in the first place?
- Do you know which data resides in the cloud, and is there a data classification scheme in place?
💡 The success of your cloud migration goes beyond KPIs; don’t forget about your people! Teams should be aligned with purpose and strategy.
What Are Common Security Concerns Associated with Cloud Migration?
- Data Loss: Most often associated with security incidents arising from human error or bad actors. Without proper backup and recovery configurations, all of your data can disappear.
- Insecure APIs: APIs are frequently configured with public IP addresses and interact with either people or machines outside the organization. Adequate controls and security configurations should be in place to mitigate this risk.
- Misconfiguration: When resources are created or updated incorrectly, it can lead to deletion, unintended modification, public exposure, or improper use of resources. Misconfiguration of cloud resources remains the most prevalent cloud vulnerability.
- Improper Identity & Access Management: Whether intentional or unintentional, access management that doesn’t follow least-privilege principles can create big problems. This can lead to unauthorized access to resources and the exfiltration, modification, and deletion of resources or data, which can be catastrophic for the organization.
- Compliance Issues: Different compliance requirements exist depending on what rules and regulations you must abide by. Non-compliance with regulations can result in hefty fines, lawsuits, and damage to organizations' reputations. To avoid this, it’s imperative to ensure you are aware of regulatory requirements and how to implement them in the cloud.
Threats are constantly evolving, so staying on top of emerging threats and risk vectors in the cloud is imperative. If you stay up to date on current threats, have a plan in place, and proper precautions are taken, the likelihood of running afoul of these risks is severely reduced.
Despite these concerns, a successful cloud migration with appropriate security measures in place can increase your organization’s security capabilities.
For example, According to an AWS whitepaper, 45% fewer security-related incidents occurred on average after a well-planned and properly executed migration to AWS.
When to Consider Security in Your Cloud Migration Plan?
According to Gartner, through 2025, 99% of cloud security failures will be the customer’s fault. To combat these risks, security should be at the core of your cloud migration strategy and integrated into every step of the process. Planning ahead to include guardrails and automation will provide peace of mind.
Depending on your company’s compliance requirements (HIPAA, SOC 2, PCI, etc.), using cloud-native tools can allow you to build controls into your environment that provide proactive security and configuration measures. This decreases the likelihood of breaches and generally makes audits easier, saving time and money in the long run. A security-minded cloud migration will vastly reduce security incidents, and having the proper plan and framework in place to build a robust security infrastructure will pay off later.
5 Steps to Creating Your Cloud Migration Security Plan
1. Understand the Shared Responsibility Model
The cloud can be more secure than an on-premise workload if configured correctly. This is partly due to the cloud service provider taking on some of the burden. That said, not all responsibility is transferred, and you are still responsible for securing your data in the cloud. Understanding where the distinction in responsibilities lies and which belongs to your organization is crucial.
An easy way to break this down is that the provider is responsible for the security of the cloud, while you are responsible for security in the cloud. An example of the AWS Shared Responsibility model can be seen here:
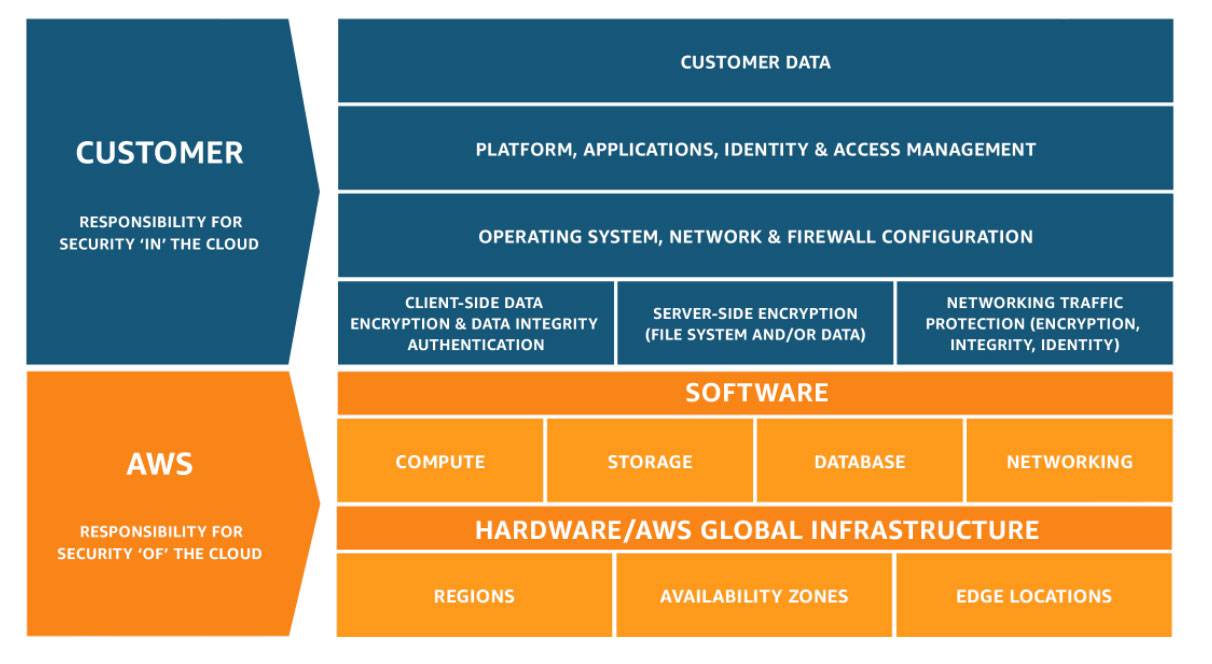
AWS Shared responsibility model
2. Create a Baseline
Before migrating to the cloud, a holistic security policy that will be implemented across all workloads should be created or adopted. This policy will be the backbone of your security infrastructure. CIS, NIST, or ISO frameworks can be used to simplify this process.
3. Audit Your Digital Assets
Take a look at your current workloads. Get to know the architectures, data, and how security is currently implemented. This will help you understand what may need to be adapted to best take advantage of cloud security capabilities.
Depending on the kind of data each workload has, there may be different compliance requirements. Ensure that any legal or regulatory requirements your data is subject to are planned for before you start your migration.
4. Build a Secure Platform
The tools and processes that you currently use in an on-premise environment aren’t always going to be applicable to a cloud environment. Remember your end goal and try not to implement tools you’ll only use for migration purposes with plans to upgrade or change them later. These are often never upgraded and are not the best tools for continuous usage. Successful implementation of cloud security requires constant integration of security into all aspects of your migration and continued cloud usage. From design through operations, baking security into your process should be the goal.
Implementing a DevSecOps model and configuring a zero-trust access model are high-level examples of how this can be done. In addition, utilizing cloud-native tools often leads to easier integration and a more seamless experience. Here are lists of security and identity tools for AWS and GCP.
5. Partner with a Cloud Security Expert
The cloud migration process (and coinciding security measures) can seem daunting. You may find yourself wondering, “Where do I start?” and “What security framework is best?”
From implementation to upkeep, partnering with a cloud security expert can be helpful. At ScaleSec, we solve complex cloud security and compliance challenges with manageable, frictionless solutions. From our security assessments to hands-on execution, we’re here to equip you with security solutions that help your team move faster. Get in touch to learn more!

