One of the notable new security services released at NEXT `19 is Google Cloud’s Event Threat Detection (ETD). This article will focus on the high level components of ETD and how you may be able to fit ETD into your current architecture.
Expect a follow up post with more technical details and examples once we’ve had a chance to get hands-on with ETD.
Source: https://cloud.google.com/event-threat-detection/
What is ETD
Event Threat Detection (ETD) aims to provide customers a managed service in which ingested log data is analyzed for potential threats using Google’s own threat intelligence and machine learning capabilities.
As many security operations professionals can attest, the number of logs captured in todays environments has skyrocketed, making it very expensive to run top SIEM and threat detection tools. ETD helps to solve this problem by analyzing the logs and only sending the discovered incidents to your SIEM tools, drastically reducing the amount of logs which are coming into your systems.
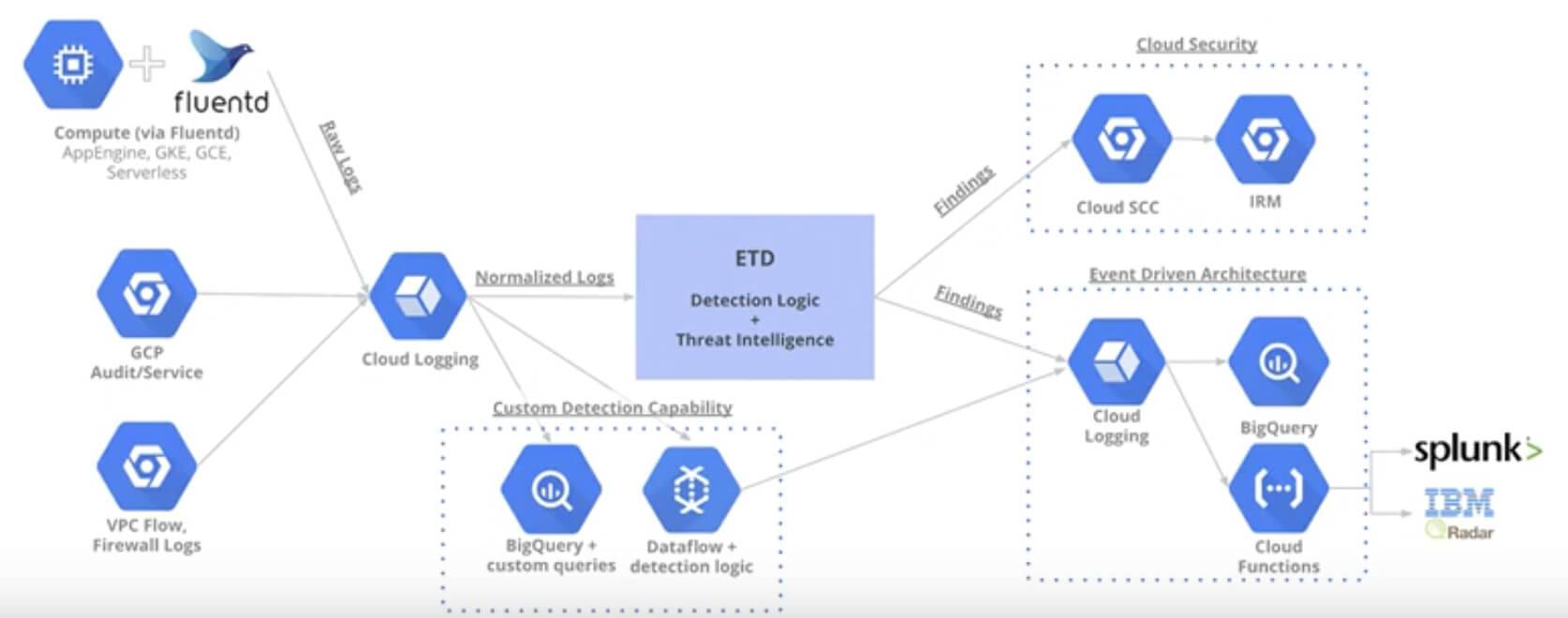
Log Sources
System logs are the foundational element from which most products are to detect threats from, ETD is no different. The following log sources are currently available to ETD:
- GCP Audit Logs
- Firewall Logs
- VPC Flow Logs
- Google Compute Instance Logs (From FluentD / Stackdriver Agent)
More log sources, including third-party integrations, are planned for future iterations of ETD.
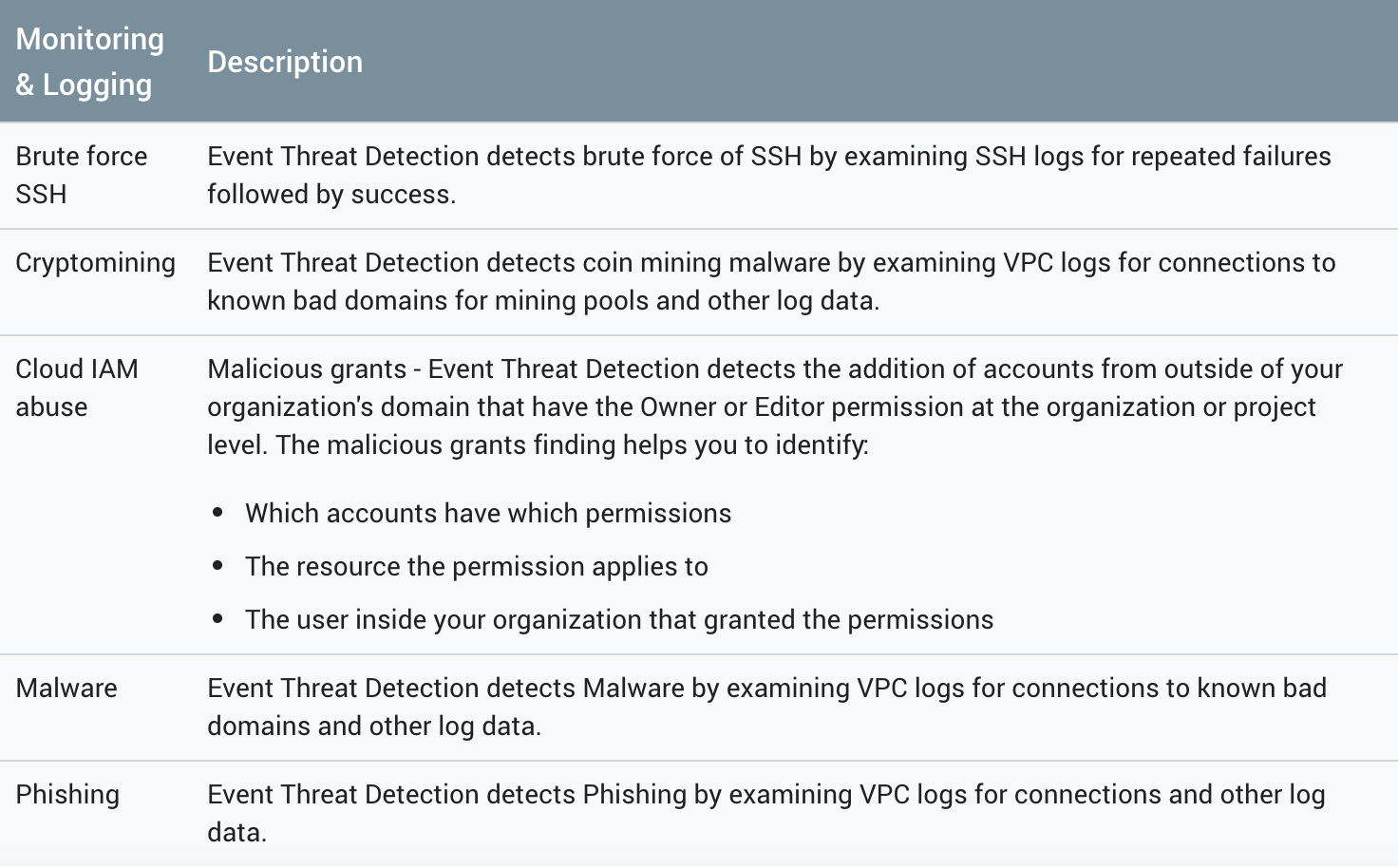
Available Threat Detection Signatures
The pre-created threat detection signatures are a big draw to teams who are just starting out on Google Cloud or do not have the existing skillsets to create their own alerts.
ETD provides the following Threat Detections out-of-the-box today:
Source: https://cloud.google.com/security-command-center/docs/how-to-view-vulnerabilities-threats#etd
Response and Remediation
The ability to detect threats is only part of the solution, in order to truly provide seamless protections to our cloud workloads, our responses to security threats must be automated in order to respond in a timely manner.
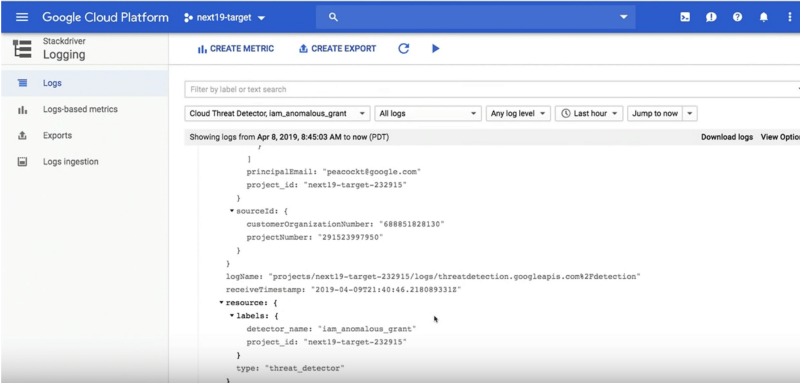
Example Event Threat Detection Stackdriver Log
ETD sends findings to Cloud Security Command Center (CSCC) for dashboard visibility and the findings are also logged in Stackdriver. These logs and alerts can then be configured to trigger an automated response to these events by triggering a CloudFunction via a pub/sub message. The CloudFunction takes the inputs from the log contents and remediates the issue in real time.
Additionally, the CloudFunction can include code to notify team members or kick off an additional workflow.
For example, if ETD detects brute force SSH attempts on an instance, the triggered CloudFunction could automatically respond by taking the following actions:
- Update the Firewall to deny a specific IP range
- Send a notification to a Slack channel (see example code here)
- Create a JIRA ticket of the incident
Custom Detection
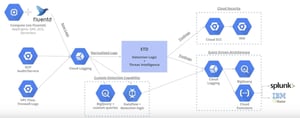
Pre-defined events are great if you are just getting started on the Google Cloud Platform, but for the advanced teams out there, ETD can be a piece of a larger threat detection architecture as shown below:

ETD in larger threat detection architectures
By leveraging Google’s managed services, threat detection teams who already have a solution in place can easily enhance their current capabilities and lower costs while continuing to utilize their previous technical investments.
Pricing
Pricing for ETD is free during beta, however, you may incur costs for services used with ETD, such as Stackdriver, Pub/Sub, CloudFunctions.
Conclusion
As cybersecurity remains to be a hot-button topic for the near future, Google Cloud continues to show progress and commitment to helping their users secure workloads and services running on GCP. ETD appears to be another great addition to the ecosystem of Google Cloud security products and closes a current gap when compared to their competitors. Look for Google Cloud to continue to be an industry leader in cloud platform security.
How can I get started with ETD?
Sign up for the private beta version of ETD here!
Thanks to Jason Dyke and Ryan Canty.