
AWS re:Invent 2022 Security Recap
ScalesSec attended AWS re:Invent 2022 last week and loved the in-person connections with our clients, partners and peers. Our focal point there, as always, was security and compliance. We are providing a high level review of everything announced during the event that involved either of these areas, or if they could potentially impact your environment’s security.
Amazon Security Lake (Preview)
Amazon Security Lake (Preview)
Amazon Security Lake (in preview) leverages the Open Cybersecurity Schema Format (OCSF) to provide a standard interface for data ingestion, from supported third parties and AWS services, to a managed data lake in AWS. This new service normalizes and centralizes security log data so responders can bring the full power of AWS Cloud to bear on security events from AWS services like CloudTrail, Security Hub findings, Route53, and VPC flow logs, and a growing list of partner technologies that support OCSF. AWS has a great blog that covers this.
Beyond the Amazon Security Lake preview, growth of the OCSF standard is exciting and is sure to be a hot topic in the coming year.
AWS Wickr

AWS Wickr
AWS Wickr is an end-to-end encrypted communication platform that allows direct messaging, group messaging, file sharing and more. Think of this as a competitor to Slack, Microsoft Teams or other messaging platforms.
Wickr allows you to manage the platform through AWS and has many features to meet regulatory requirements. Additionally, having default end-to-end encryption is not the case on all messaging platforms. AWS released a well-written blog going into more details.
AWS Config Rules - Proactive Mode
AWS Config
AWS Config is a service that regularly scans supported resource types for non-compliant AWS configuration settings after they have been deployed. Even with auto-remediation enabled, a misconfiguration could be introduced between regularly scheduled compliance checks.
To close this window of exposure, AWS announced that Config rules can now be run prior to pushing configuration settings in a proactive mode as a step in your build pipeline. This will allow you to identify and remediate misconfigurations prior to deployment.
AWS Control Tower - Comprehensive Controls Management (Preview)
AWS Control Tower
AWS Control Tower is a service that allows you to build and manage secure multi-account environments in AWS, ensuring that these environments are running security best practice guardrails before production use.
Now in Preview, AWS Control Tower – Comprehensive Controls Management simplifies the application of controls by service, control objective or compliance framework across environments managed by Control Tower. These controls can be proactive, detective or preventive. This allows you to ensure that you are meeting your compliance requirements in new environments with AWS handling the controls mapping.
AWS CloudWatch Logs - Protecting Sensitive Data

AWS CloudWatch Logs - Protecting Sensitive Data
CloudWatch Logs are used to monitor, store and access your log files. In the past, sanitization and auditing of sensitive information was a manual process that required careful coding or intervention/transformation prior to aggregation. With the new data protection feature in CloudWatch Logs, users can set masking policies based on predefined identifiers, restrict access to unmasking using standard AWS IAM permissions, and automate audit and monitoring processes for easier management and compliance.
AWS CloudWatch Cross-Account Observability
AWS CloudWatch Cross-Account Observability
AWS CloudWatch is used to monitor cloud resources and applications. It can track metrics, set alerts and collect logs (as mentioned above). Historically, CloudWatch has been bound by the account and observing metrics/logs/events from another account would require additional resources and potentially costly orchestration.
Amazon CloudWatch Cross-Account Observability allows users to easily observe CloudWatch data across any account in the same region. With some relatively simple initial configuration, CloudWatch data from disparate accounts can easily be rolled up to a centralized monitoring account.
AWS Verified Access
AWS Verified Access
AWS Verified Access is a new service in preview that allows you connectivity to corporate applications without using a managed VPN service. This is using zero trust security principles that move away from network level controls and more into identity based controls. Users will be verified via AWS Identity Center via browser plug-ins. No need to continually reconnect to VPNs throughout the day. AWS has a great blog on setting this up.
Amazon VPC Lattice
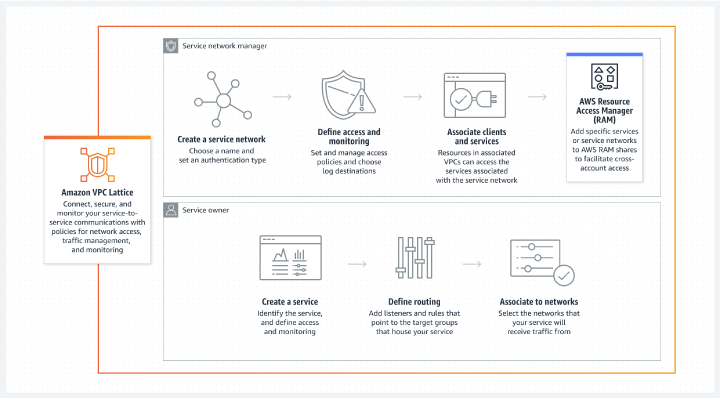
Amazon VPC Lattice
Amazon VPC Lattice is a new overlay network offering that connects and secures containers, instances, and lambdas with and across VPCs/Accounts. Native IAM policies can be applied to “services” and “networks” to enforce access policy as code. An AWS blog runs through the creation of a VPC lattice.
AWS KMS External Key Storage
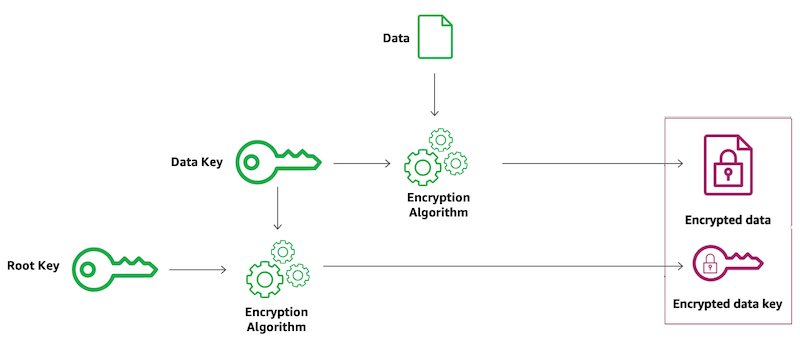
External Key Store
Key Management Service (KMS) is a service that handles keys within the cloud. Previously, KMS either generated and stored keys for customers or allowed the importation of keys generated by a customer in either the managed service or an in-cloud but customer managed CloudHSM instance. KMS can now connect to an External Key Store, where the customer managed keys are stored outside of AWS.
Using keys stored outside the cloud comes with substantial operational risk. Unless this is a regulatory requirement for your organization, we recommend skipping this feature.
Amazon Inspector - Lambda Function Scanning

Amazon Inspector - Lambda Function Scanning
Amazon inspector is a service that performs vulnerability management for your EC2 instances and container workloads. With this release, Inspector now supports the scanning of Lambdas written in Java, NodeJS and Python.
Amazon Macie - Automated Data Discovery
Amazon Macie is a service that will scan your S3 bucket contents for Personally Identifiable Information (PII) or sensitive data and gives you visibility into where your data is. It uses ML to scan buckets that you define and can identify public or unencrypted buckets.
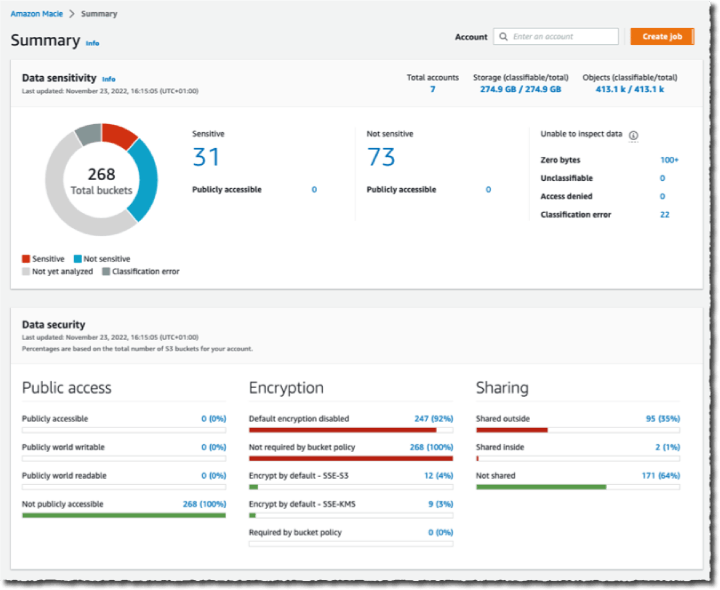
Amazon Macie - Automated Data Discovery
Automated data discovery is run at the AWS organizations level. It allows for continual discovery of data and evaluates the sensitivity of each of your buckets. New buckets created in the organization would be included in this discovery. It also reduces the operational costs and time to discover by using sampling rather than scanning an entire dataset continuously.
Amazon Verified Permissions (Preview)
Amazon Verified Permissions
Amazon Verified Permissions is a new service in preview that allows application developers to let their end users manage permissions and share access to data. This simplifies changing and updating permissions rules by having them in a centrally managed location. This data is auditable and can manage fine-grained permissions. An AWS blog gives a short summary.
AWS Backup - Protect CloudFormation Stacks
CloudFormation Stacks are infrastructure as code used to create and manage AWS environments. AWS Backup is a service used to backup and restore AWS services, including CloudFormation Stacks. When Backup is backing up a Stack it gives you a single recovery point, meaning that changes to data protection policies after this point aren’t captured.
AWS Backup - Protect CloudFormation Stacks
Backups will now keep track of these changes and update your data protection policies when you restore from the last backup.
Summary
While AWS re:Invent and re:Inforce have a large amount of product releases, AWS frequently releases many more throughout the year. Connect with ScaleSec to help keep track of how to keep your environment secure.
