
CoreKinect
United States
PLATFORM
AWS GovCloud
CoreKinect builds rugged IoT tracking solutions for assets and personnel, delivering real-time data to support operational awareness for first responders, firefighters, and more. CoreKinect’s customers require high standards for security, reliability, and regulatory compliance.
Challenge
CoreKinect builds hardware devices with embedded software to communicate with a web-based backend platform. They initially deployed the backend as a proof of concept to facilitate development and testing, and contacted ScaleSec to build production-quality infrastructure to meet necessary security and compliance standards.
In particular, CoreKinect is seeking US federal government customers, requiring authorization under the Federal Risk and Authorization Management Program (FedRAMP). CoreKinect sought to meet FedRAMP requirements at the moderate impact level.
Additionally, CoreKinect’s web services were initially built without cloud considerations like containerization, deployment automation, and utilization of managed services. These considerations needed to be addressed to meet reliability and security goals.
Solution
ScaleSec recommended migrating to AWS by establishing an AWS GovCloud landing zone, replatforming the application to leverage AWS managed services, and integrating AWS security services aligned with NIST SP 800-53 revision 5.
ScaleSec created new accounts in both AWS commercial and GovCloud (US) partitions, and configured AWS Organizations for account management. Separate accounts were used to provide strict segmentations between network, security services, log archival, management, and application environments. Core security services are centralized, including logging via AWS CloudTrail with alerts on high-risk events, configuration monitoring via AWS Security Hub and AWS Config rules, and threat detection via Amazon GuardDuty. Service Control Policies restrict unapproved or unnecessary actions, such as root user actions or non-compliant services. User access is managed by AWS IAM Identity Center for temporary, least privileged permissions.
To support network inspection requirements, a transit VPC network architecture was selected. AWS Network Firewall inspects traffic leaving the network or crossing internal network zones. VPCs provisioned in separate accounts direct outbound traffic through the central inspection VPC. Separate subnets segment resources between management and application services, as well as public and private services. Each VPC requires DNSSEC validation using Amazon Route 53 Resolver.
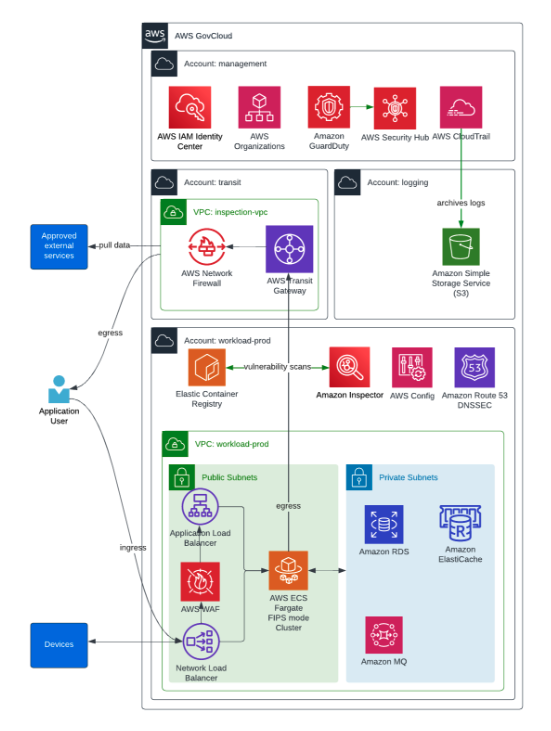
To minimize operational overhead, enhance security posture, and enable scalability, the application was replatformed to support deployment on AWS Fargate. The application was initially written using .NET Framework version 4.8, which only supports deployment on Microsoft Windows. CoreKinect upgraded the application components to .NET 7, which supports Linux deployments. Components are deployed as Fargate services to a FIPS-mode cluster. The application’s traffic patterns are unpredictable, as device usage varies dramatically without notice. Each Fargate service tracks target metrics and automatically scales the number of service tasks to meet traffic demand.
Some of the application components use non-standard network protocols, so inbound traffic is first directed to a Network Load Balancer (NLB) using AWS Elastic Load Balancing. The NLB then directs traffic either directly to those services, or to an Application Load Balancer (ALB) for TLS termination. The ALB integrates with an AWS Web Application Firewall (WAF) to block potentially malicious requests before they are forwarded to the application. Additional supporting services were replatformed to AWS managed services to improve reliability and minimize operational burden, including Amazon Elasticache for Redis, Amazon MQ for RabbitMQ, and Amazon RDS for databases.
ScaleSec also built an application deployment pipeline with integrated security scanning. All application components are defined and deployed using AWS CloudFormation, with parameters and secrets in AWS Systems Manager or AWS Secrets Manager. Developers upload new container images to Amazon Elastic Container Registry (ECR) which automatically scans for vulnerabilities using Amazon Inspector, both on push and on a continuous basis. This triggers AWS CodePipeline to perform blue/green deployments via AWS CodeDeploy. The blue/green deployment strategy ensures the updated application is healthy before traffic is redirected, and automatically rolled back if the application fails to reach a healthy state.