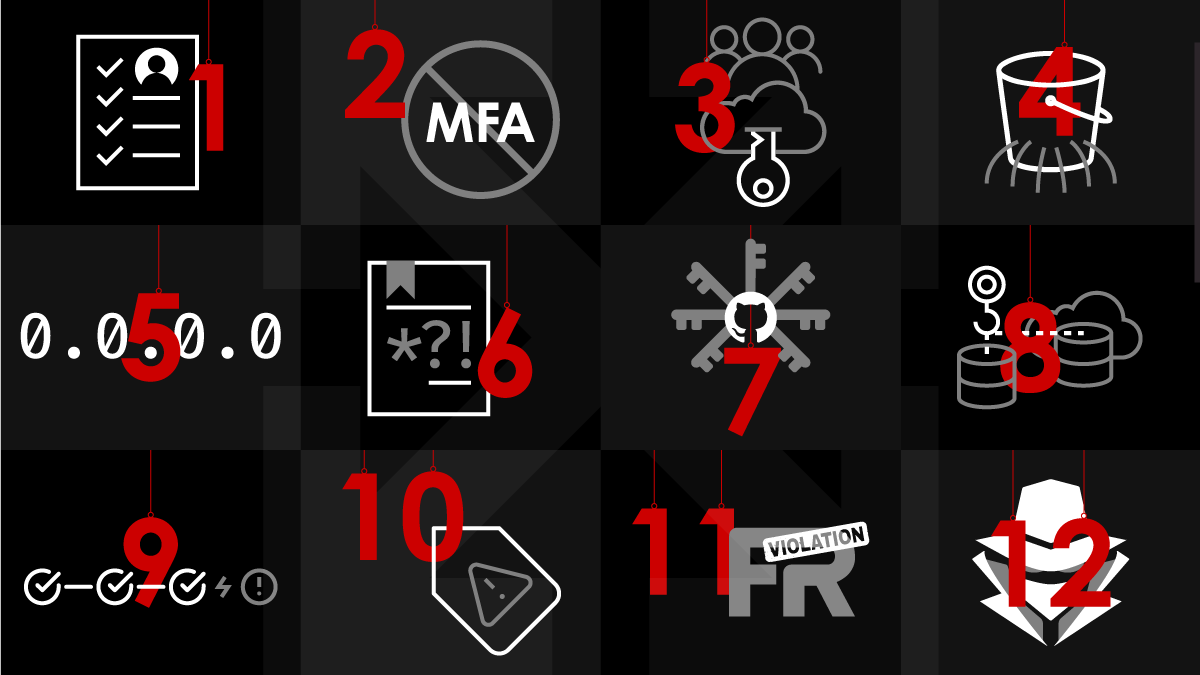
12 Days of Cloud Security Christmas
The Cloud is the gift that keeps on giving with new features and services being deployed daily. Securing your Cloud environment is an add-on that makes your gift extra special. Similar to the Cloud, users continue gift-giving traditions well after the holiday is over. From wide open S3 buckets to FedRAMP violations, security misconfiguration continues to be on the list of gifts security teams receive throughout the year. This holiday season, let the 12 days of Cloud Security Christmas bring a smile to your face as you recount some of the joys that you have experienced through the year with your cyber security team.
On the first day of Christmas a User gave to me
A malformed IAM policy.
On the second day of Christmas a User gave to me
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the third day of Christmas a User gave to me
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the fourth day of Christmas a User gave to me
Four S3 buckets with wide open bucket policies,
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the fifth day of Christmas a User gave to me
Five network rules with 0.0.0.0 access for everybody,
Four S3 buckets with wide open bucket policies,
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the sixth day of Christmas a User gave to me
Six reasons why we don’t need a password policy,
Five network rules with 0.0.0.0 access for everybody,
Four S3 buckets with wide open bucket policies,
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the seventh day of Christmas a User gave to me
Seven secret keys in Github,
Six reasons why we don’t need a password policy,
Five network rules with 0.0.0.0 access for everybody,
Four S3 buckets with wide open bucket policies,
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the eighth day of Christmas a User gave to me
Eight lift and shift projects,
Seven secret keys in Github,
Six reasons why we don’t need a password policy,
Five network rules with 0.0.0.0 access for everybody,
Four S3 buckets with wide open bucket policies,
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the ninth day of Christmas a User gave to me
Nine broken CI/CD pipelines,
Eight lift and shift projects,
Seven secret keys in Github,
Six reasons why we don’t need a password policy,
Five network rules with 0.0.0.0 access for everybody,
Four S3 buckets with wide open bucket policies,
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the tenth day of Christmas a User gave to me
Ten systems without tags,
Nine broken CI/CD pipelines,
Eight lift and shift projects,
Seven secret keys in Github,
Six reasons why we don’t need a password policy,
Five network rules with 0.0.0.0 access for everybody,
Four S3 buckets with wide open bucket policies,
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the eleventh day of Christmas a User gave to me
Eleven FedRAMP violations,
Ten systems without tags,
Nine broken CI/CD pipelines,
Eight lift and shift projects,
Seven secret keys in Github,
Six reasons why we don’t need a password policy,
Five network rules with 0.0.0.0 access for everybody,
Four S3 buckets with wide open bucket policies,
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
On the twelfth day of Christmas a User gave to me
Twelve security breaches,
Eleven FedRAMP violations,
Ten systems without tags,
Nine broken CI/CD pipelines,
Eight lift and shift projects,
Seven secret keys in Github,
Six reasons why we don’t need a password policy,
Five network rules with 0.0.0.0 access for everybody,
Four S3 buckets with wide open bucket policies,
Three root accounts with access keys,
Two reasons why MFA should not be a security thing,
And a malformed IAM policy.
Happy Holidays, Merry Christmas, and a Secure New Year from ScaleSec!
