AWS Control Tower Guardrail Alignment

Modernizing Security: AWS Series - AWS Control Tower Guardrail Alignment
Well-Architected Framework Overview
The AWS Well-Architected Framework is a managed tool and offering that gives cloud architects access to the knowledge developed over a broad amount of architectural reviews with customers. The framework ensures that customers are aware of best practices in order to reduce architectural risks. The Well-Architected Framework provides a consistent approach for evaluating systems based on the qualities expected from modern cloud-based workloads. The framework is based on five pillars: Security, Reliability, Performance, Cost Optimization and Operational Excellence, and is designed to provide guidance so that customers are able to achieve optimal value from Amazon Web Services.
Control Tower Overview
In alignment with the Well-Architected Framework guidance, AWS Control Tower allows organizations to deploy AWS accounts with guardrails based on security and compliance best practices. AWS Control Tower automates the setup of a new landing zone using blueprints for identity, federated access, and account structure.
This article will focus on the 11 Well-Architected security controls and aim to provide further insight on how AWS Control Tower, accompanied with additional guardrails, can help address those controls while mitigating risks.
As an example below, you can see the following high-level architecture overview of how AWS GuardDuty and CloudTrail are designed and deployed across accounts as a baseline, as part of the control-tower deployment process.
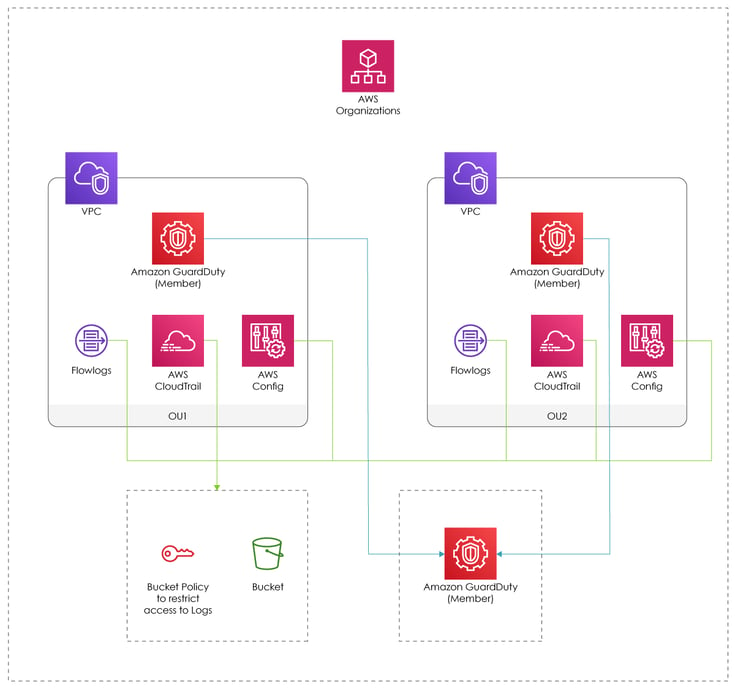
AWS Control Tower Overview
In addition to other services shown in the diagram, such as AWS Config and VPC Flow Logs, GuardDuty and CloudTrail are centralized and aggregate critical API logs and event data across the AWS organization accounts. Nonetheless, additional resources can always be added to the baseline templates by customizing the Landing-zone blueprints.
Sec-04-05 Detect, Defend and Investigate Security Events
By default, CloudTrail logging is enabled for all accounts orchestrated via Landing Zone.
CloudTrail logs are consolidated in a single, centralized bucket inside the logging(audit) account and can also be enabled with automated log streaming to CloudWatch to capture live API events within each account.
GuardDuty is an AWS Native ML threat detection solution that relies on both CloudTrail and VPC Flow Logs that provides threat intelligence feeds like lists of malicious IPs and domains and identifies unauthorized reconnaissance activity within your AWS Organization.
GuardDuty also provides extensive capabilities and functionalities as a behavior-based detection system to alert incident response teams for any suspicious API events.
In the following diagram, we present a case study where GuardDuty events are centralized within the master security account while streaming its events to SecurityHub to provide a comprehensive view of high-priority alerts.
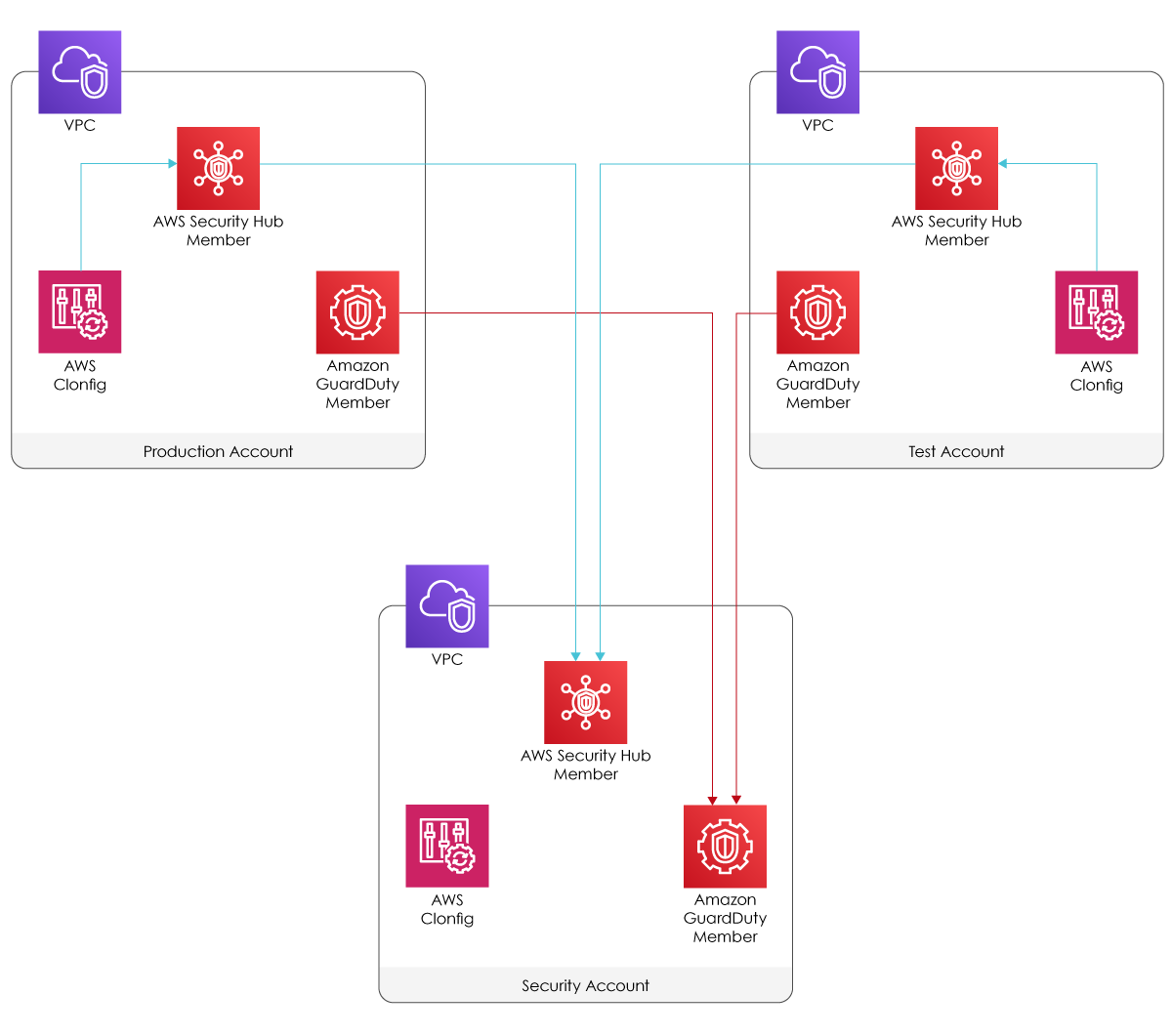
Detect, Defend, and Investigate Security Events
In this scenario, GuardDuty, Cloud Trail and Security Hub play an important role in protecting your AWS infrastructure by monitoring and establishing meaningful incident response plans that follow the Well Architected Framework to follow Sec-11 control.
Sec-01-03 Programmatic Keys and Human Credentials Management Access
One of the main objectives of control tower is to enforce a single point of governance for critical resources in separated accounts while exercising least privileges policies and identity management (IAM) centralization.
To impose a strong security access posture very restrictive IAM roles and policies are created as part of the deployment process. This is to allow specific services cross account access as required for logs and security events that stream to the core accounts.
Additional roles or resources such as IAMIdentity Provider can be also created as a baseline to automatically federate your AWS accounts with your organization’s identity management solution. This is done natively via IAM SAML integration, which can reduce significant operational overhead for enterprise customers.
In the following sequence, you will find an example of a declarative block within the landing-zone manifest file which aims to create two roles (Admin and ReadOnly); which will later-on get mapped to an identity provider user pools (such as ADFS, Okta etc).
The Cloudformation template that creates the roles and SAML Identity Provider is the aws-landing-zone-security.json.
core_resources:
- name: SecurityRoles
template_file: templates/core_accounts/aws-landing-
zone-security.template
parameter_file: parameters/core_accounts/aws-landing-
zone-security.json
deploy_method: stack_set
ssm_parameters:
- name: /org/member/security/admin_role_arn
value: $[output_CrossAccountAdminRole]
- name: /org/member/security/readonly_role_arn
value: $[output_CrossAccountReadOnlyRole]
Sec-06-07 Compute and Network Protection
An Amazon VPC configures the initial network for each of the Landing Zone provisioned accounts. This includes deleting the default VPC in all regions, deploying the Account Vending Machine requested network type, and network peering with the Shared Services VPC when applicable.
As mentioned prior, based on each use case, organizations can customize the default blueprints with their own unique VPC and Subnet network configuration. This process allows for organizations to enable segregation with requested CIDR ranges and automating their network connectivity back to on-prem via Transit Gateway solution.
Sec-08 Data Classification
Data classification is being used to help organizations make determinations for safeguarding sensitive or critical data with appropriate levels of protection.
By pre-defining Landing Zone baseline resources with a tag, organizations can identify the corresponding data classification.
Sec-09 Data Protection at Rest
AWS Control Tower uses Amazon S3 buckets and Amazon DynamoDB databases that are encrypted at rest by using Amazon S3-Managed Keys (SSE-S3) in support of your landing zone. This encryption is configured by default when you set up your landing zone. You can also establish encryption at rest for the services you use in your landing zone for the services that support it. For more information, see the security chapter of that service’s online documentation.
Sec-10 Data Protection in Transit
AWS Control Tower uses Transport Layer Security (TLS) and client-side encryption for encryption in transit in support of your landing zone. In addition, accessing AWS Control Tower requires using the console, which can only be accessed through an HTTPS endpoint. This encryption is configured by default when you set up your landing zone.
Conclusion
Whether you are a new AWS customer looking to safely land on the AWS cloud with self-service guardrails, or an existing AWS customer, Control Tower enables you to quickly set up a secure by default, multi-account AWS environment based on AWS best practices.
DISCLAIMER: AWS Control Tower can help organizations deploy secure by-default multi-account AWS environments based on best practices; however, the customer is still responsible for the day-to-day operations to protect its workloads as guided by the Well-Architected Framework.
Connect with ScaleSec for AWS business
ScaleSec is an APN Consulting Partner guiding AWS customers through security and compliance challenges. ScaleSec’s compliance advisory and implementation services help teams leverage cloud-native services on AWS. We are hiring!
Connect with ScaleSec for AWS business.
